Introduction
In this lab, you'll embark on an exciting journey into the world of network analysis using Wireshark, a powerful tool in the cybersecurity field. Imagine you're a digital detective, tasked with understanding the complex conversations happening on a computer network. How do you see what's really going on beneath the surface? This is where Wireshark comes in.
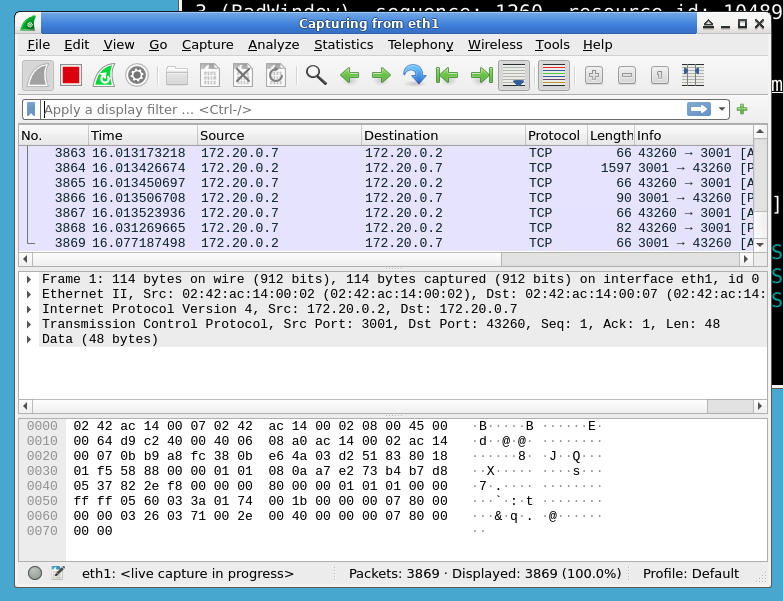
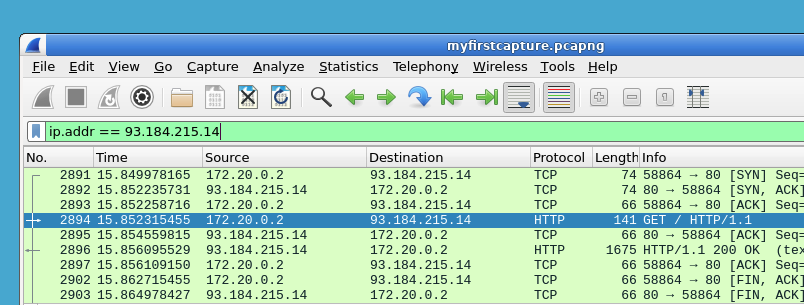
Wireshark is like a microscope for network traffic. It allows you to capture and inspect the data traveling across a network in real-time. This capability is crucial for troubleshooting network issues, detecting unusual activity, and understanding how applications communicate.
By the end of this lab, you'll have hands-on experience with:
- Installing and setting up Wireshark
- Capturing network traffic
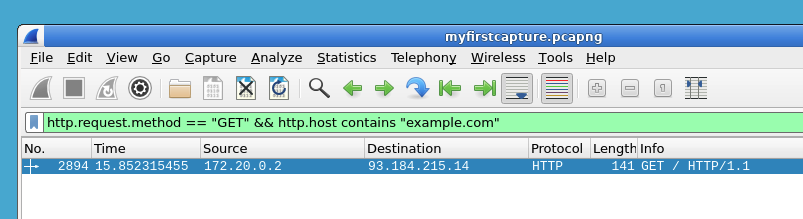
- Analyzing packet data
- Filtering network captures
- Identifying common protocols
Let's dive into the fascinating world of network analysis!