Introduction
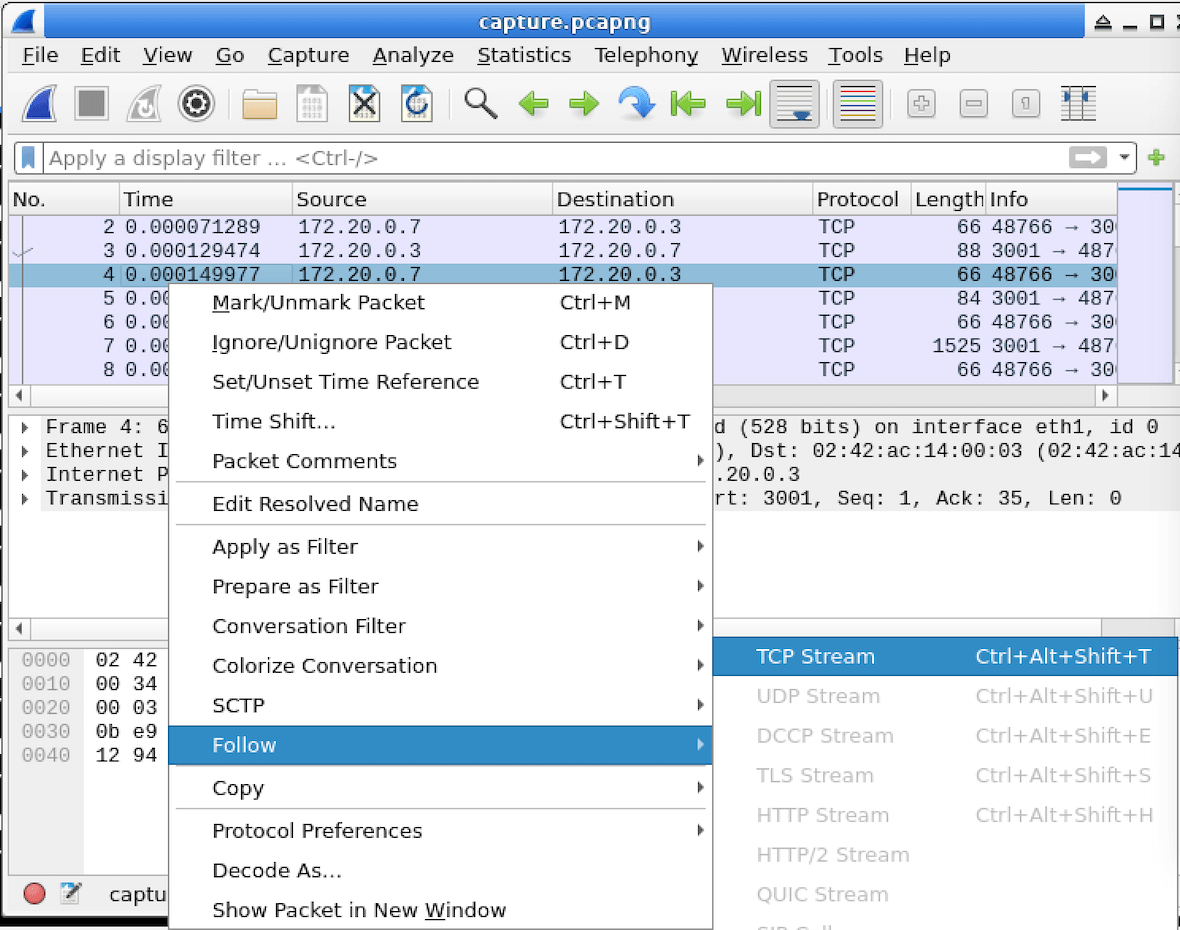
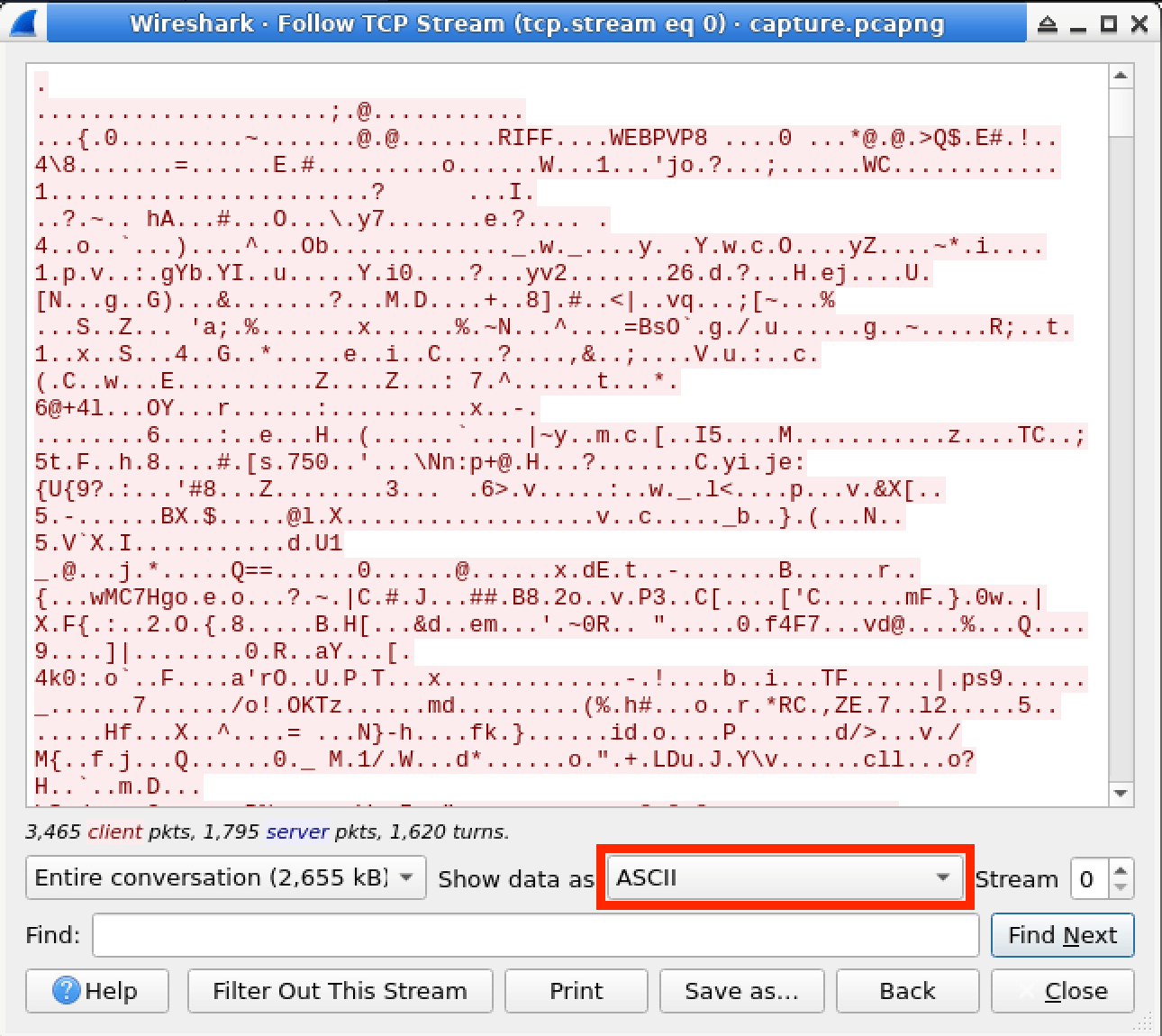
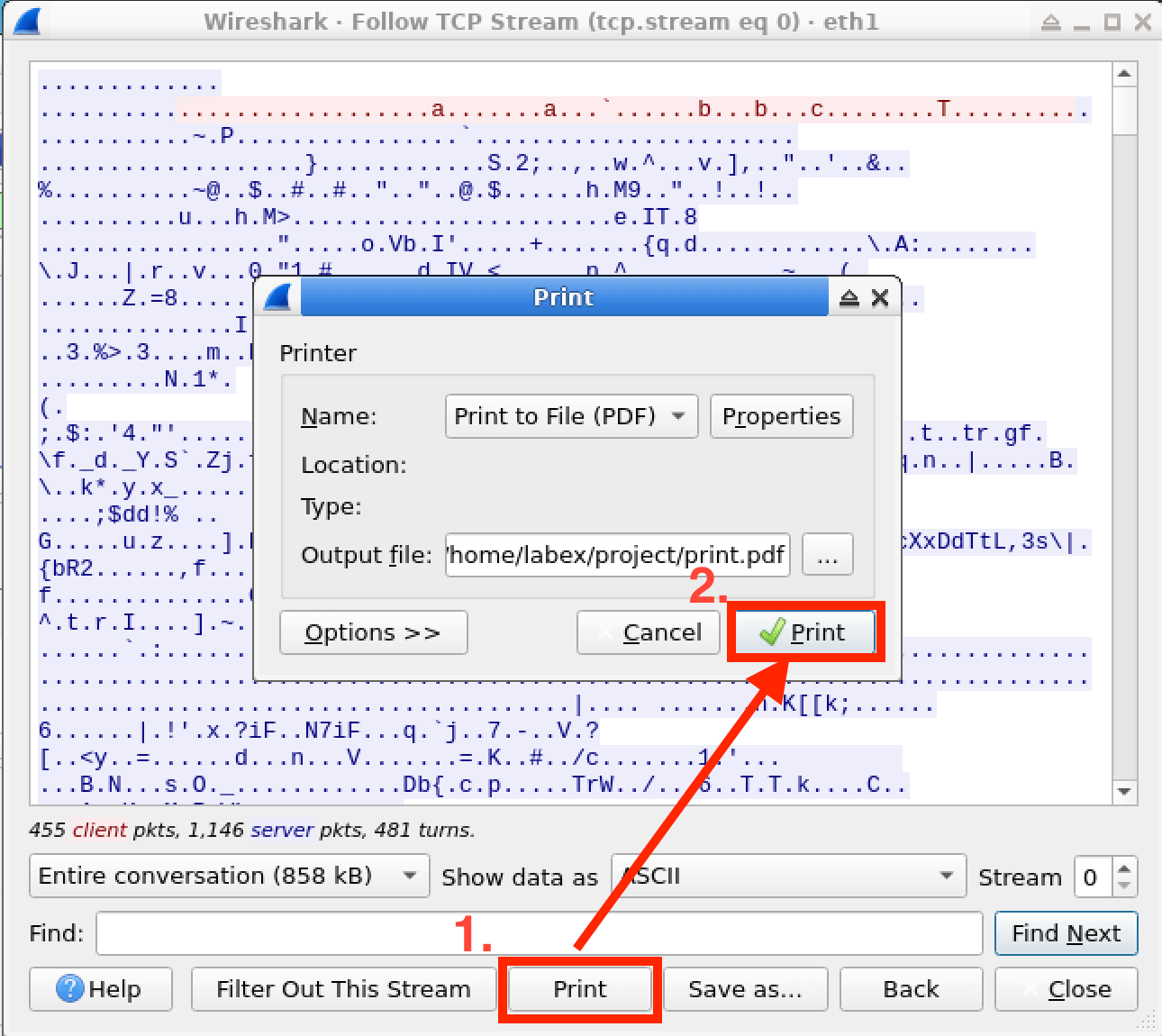
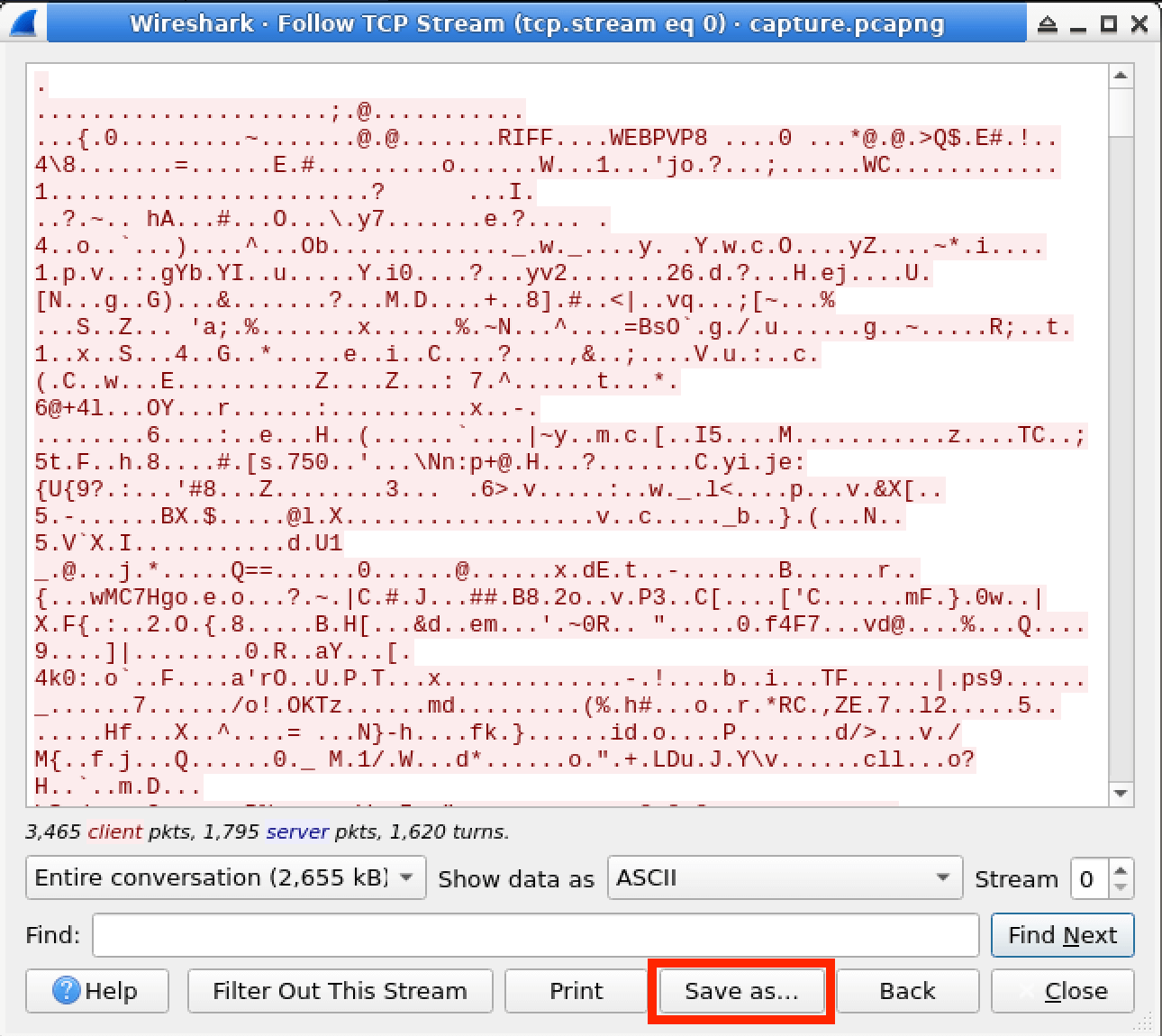
In this lab, you will learn how to use the "Follow TCP Stream" feature in Wireshark to analyze and inspect TCP traffic. This feature allows you to extract and view the data payload of a specific TCP conversation, which can be helpful in various cybersecurity scenarios, such as investigating suspicious network traffic, analyzing application protocols, or troubleshooting network issues. By the end of this lab, you will have a better understanding of how to use this powerful tool to gain insights into network communications.