Introduction
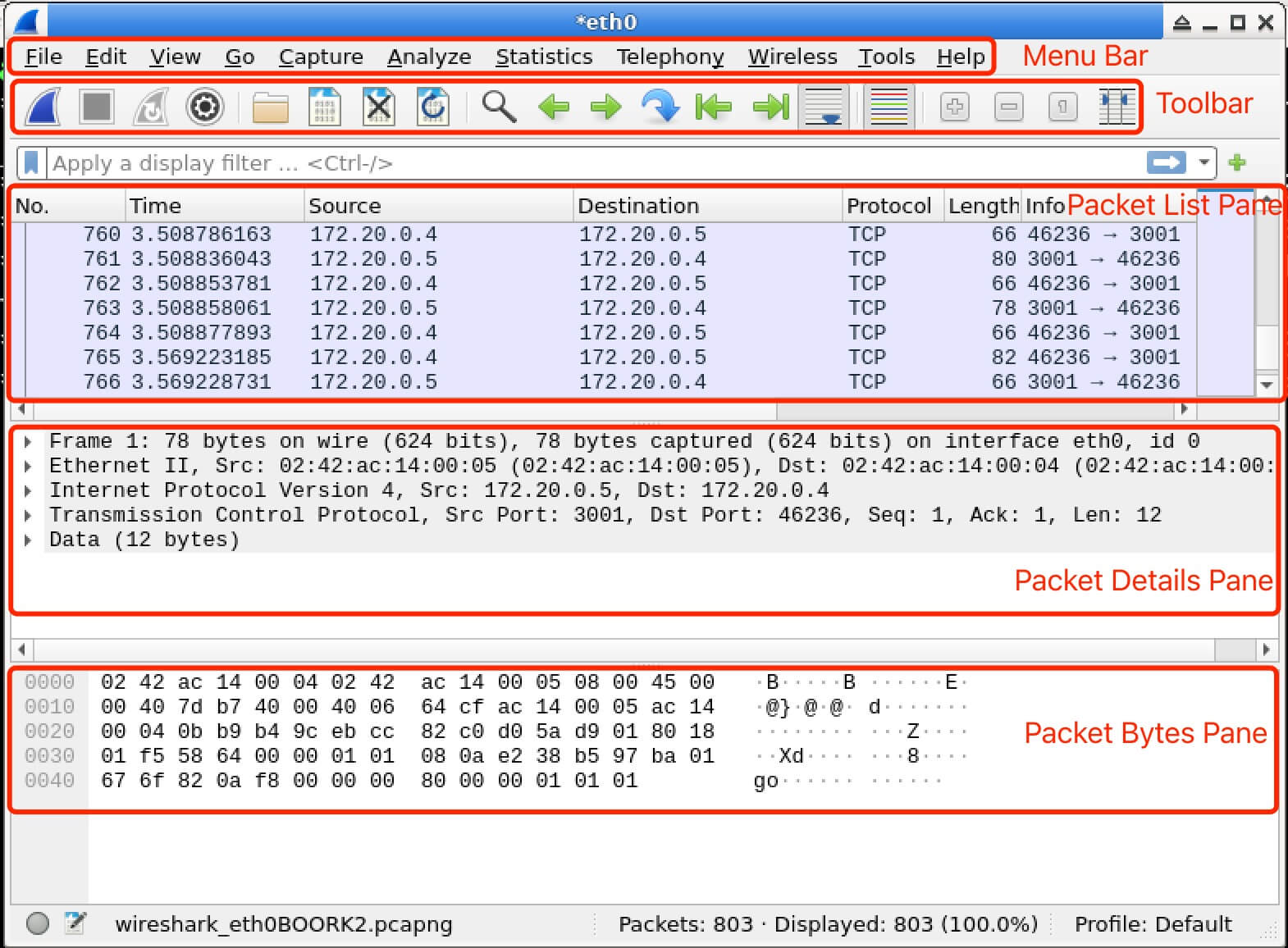
In this lab, you will learn about the Wireshark interface and its various components, which is essential for performing network traffic analysis and troubleshooting. You will explore the different parts of the Wireshark GUI, understand their functionalities, and gain hands-on experience in navigating and customizing the interface to suit your needs.