Introduction
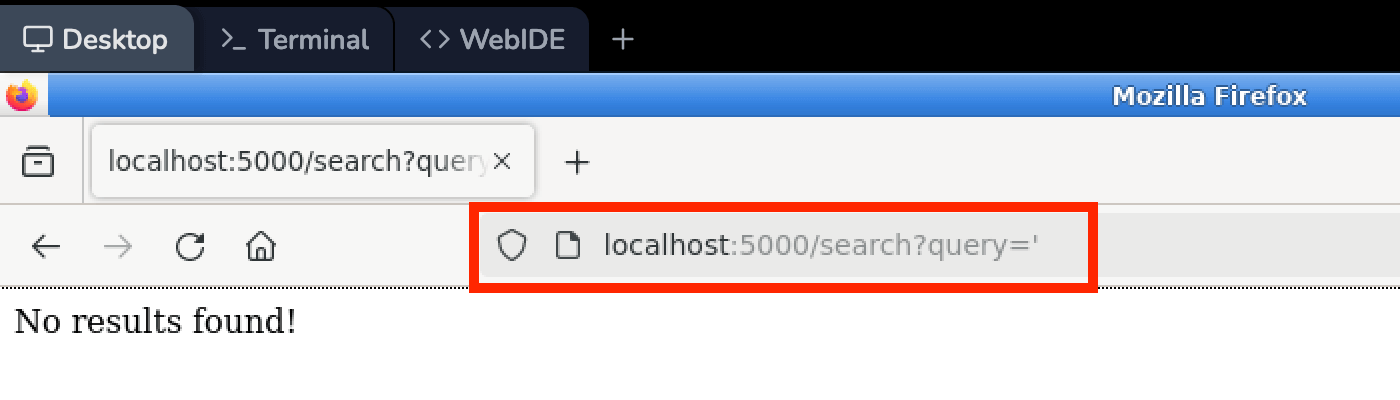
In this lab, you will learn about SQL injection, a technique used by attackers to exploit vulnerabilities in web applications that interact with databases. SQL injection attacks can allow unauthorized access to sensitive data, data manipulation, and even complete system compromise.
The objective of this lab is to gain hands-on experience with SQL injection by exploiting vulnerabilities in a vulnerable web application. You will learn how to identify potential SQL injection vulnerabilities, craft malicious SQL queries, and extract sensitive information from the database. Additionally, you will learn about defense mechanisms and best practices to mitigate SQL injection attacks.