Introduction
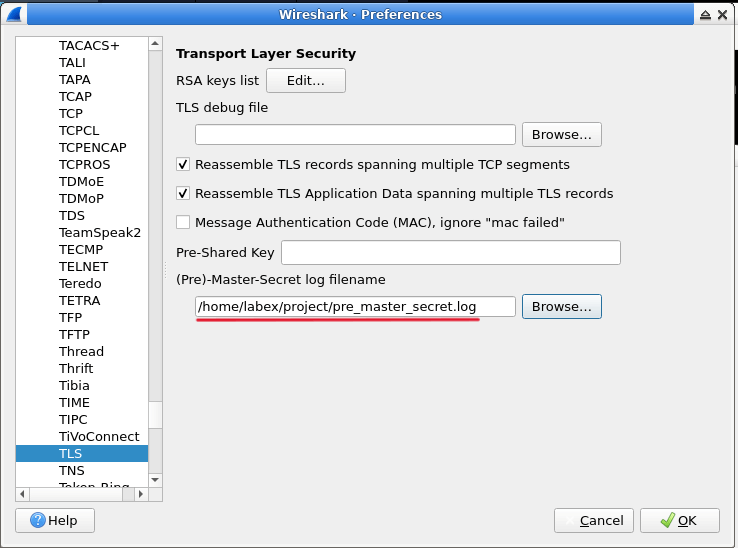
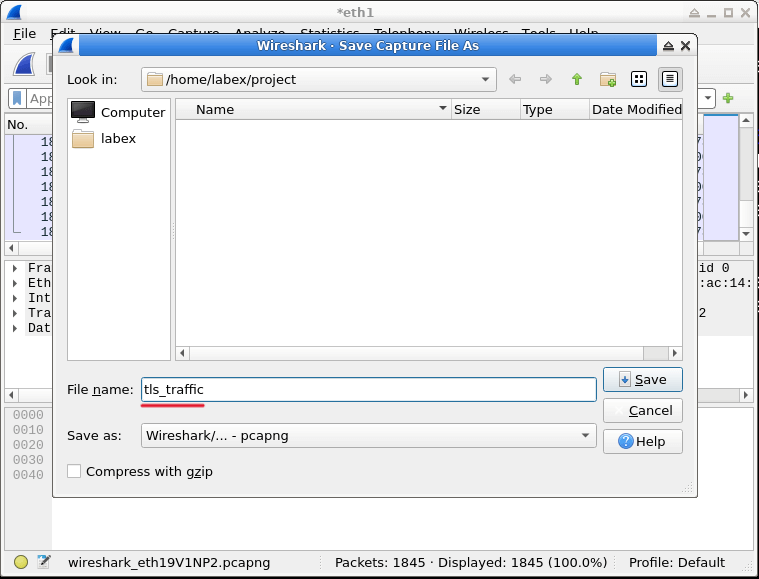
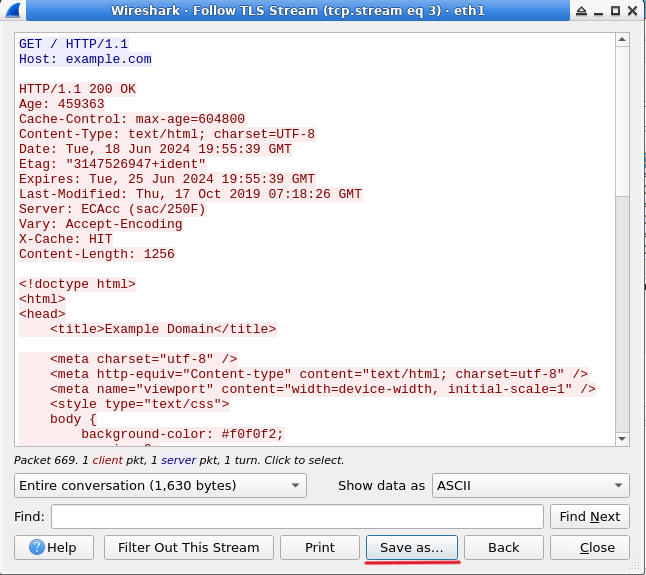
In this lab, you will learn how to decrypt SSL/TLS traffic using Wireshark, a popular network protocol analyzer. SSL/TLS encryption is widely used to secure internet communications, but in certain scenarios, such as troubleshooting or security analysis, it may be necessary to decrypt the encrypted traffic. This lab will guide you through the process of setting up Wireshark to decrypt SSL/TLS traffic, providing you with hands-on experience in a controlled environment.