Introduction
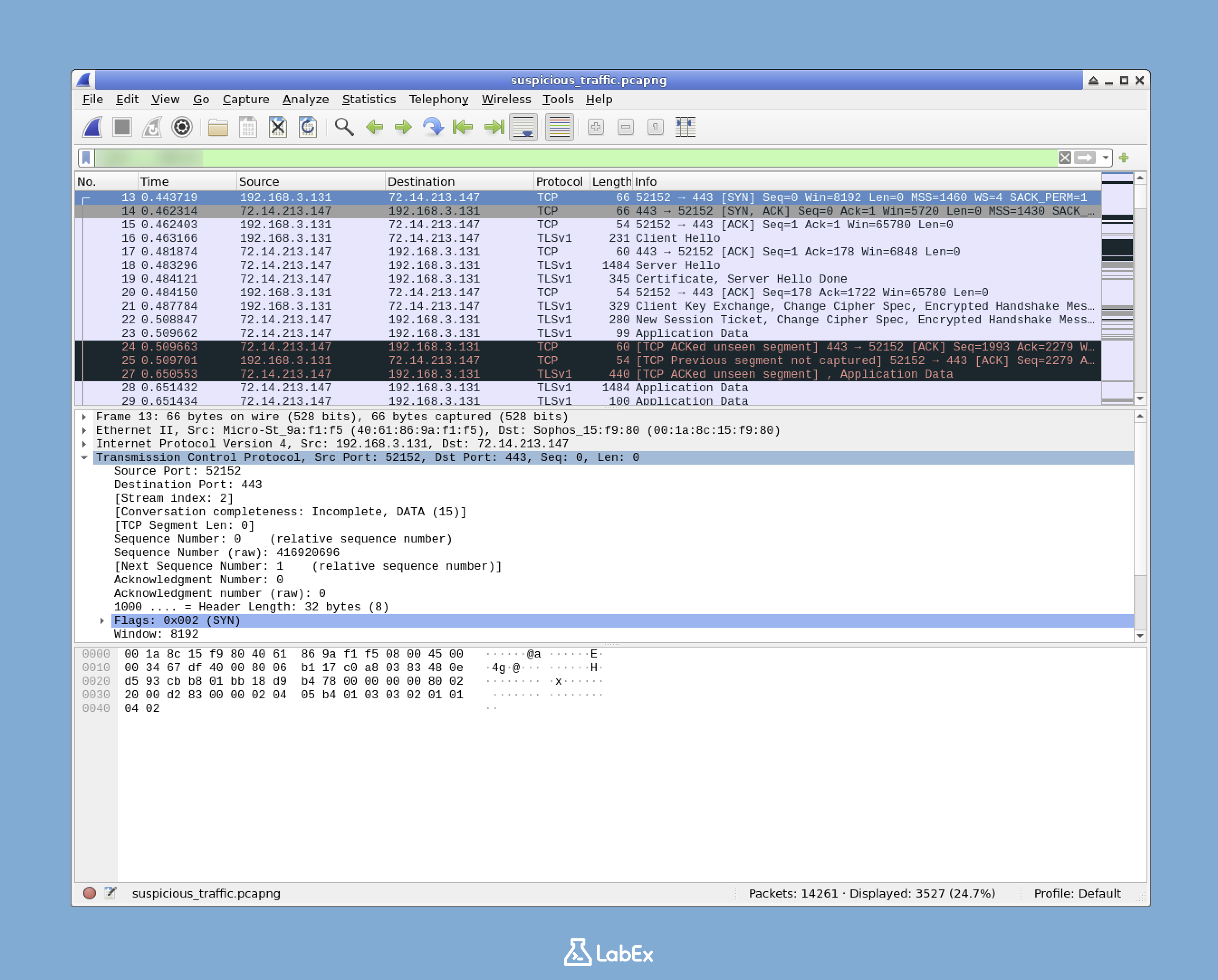
In this challenge, you will step into the role of a junior cybersecurity analyst investigating a potential data breach at Cybertech Industries. The security team has detected unusual network activity during off-hours and provided you with a packet capture file containing the suspicious network traffic.
Your task is to use Wireshark to analyze the provided packet capture file by creating a display filter that isolates only the encrypted HTTPS traffic (TCP port 443). This filtering technique will help you focus on potentially sensitive communications that may be related to the suspected breach. Once you've created the appropriate filter, you'll save it to a text file for documentation purposes.