Introduction
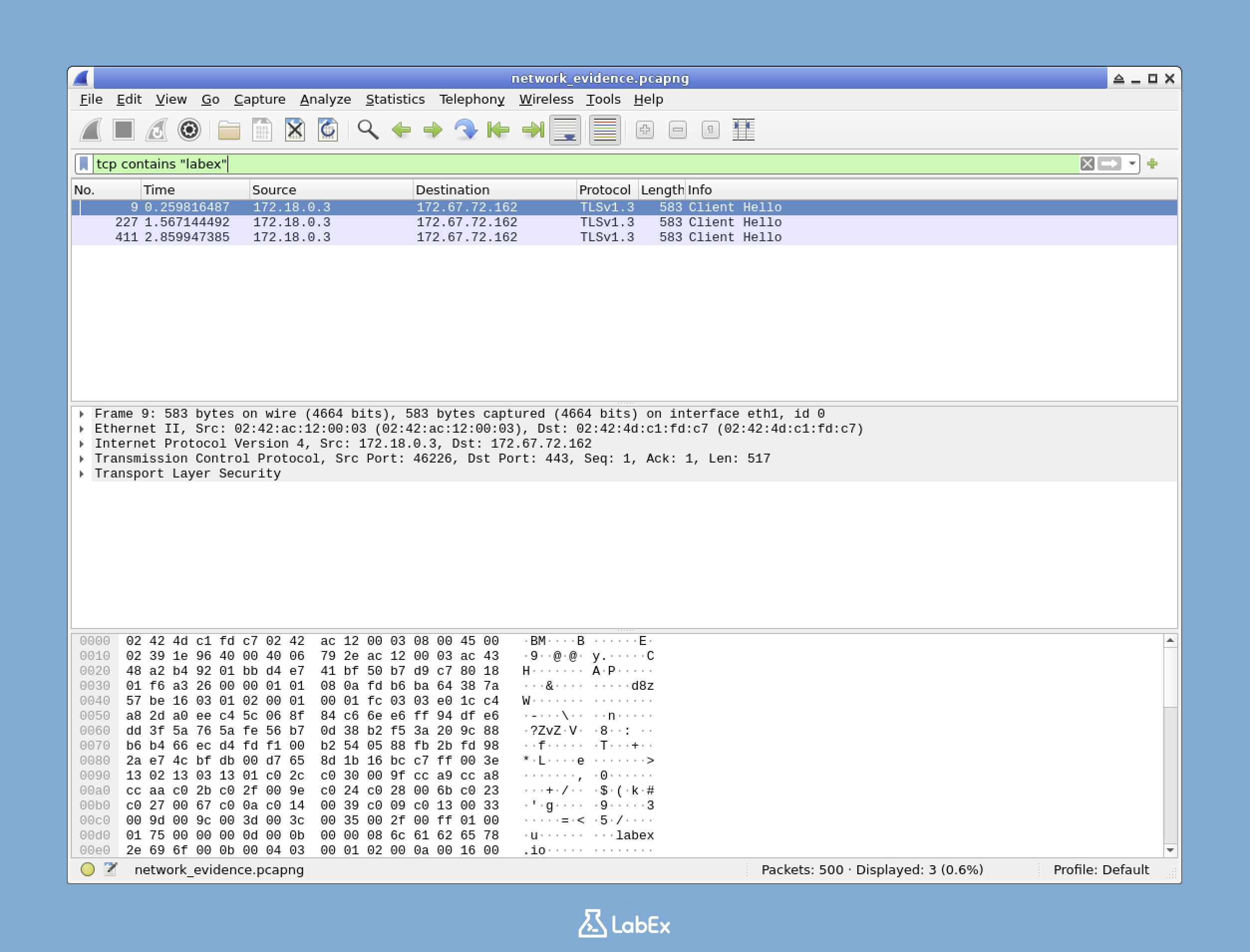
In this challenge, you will step into the role of a cybersecurity trainee at NetDefenders investigating a potential data leak. Your instructor has provided a network traffic capture file, and your mission is to extract communication evidence between an employee and labex.io for your forensic training report.
Using Wireshark, you'll analyze the captured network traffic by filtering for TCP packets containing "labex," following the TCP stream to examine the complete conversation, and saving the evidence as a text file. This practical exercise demonstrates essential network forensics techniques used by security professionals to identify and document suspicious web communications.