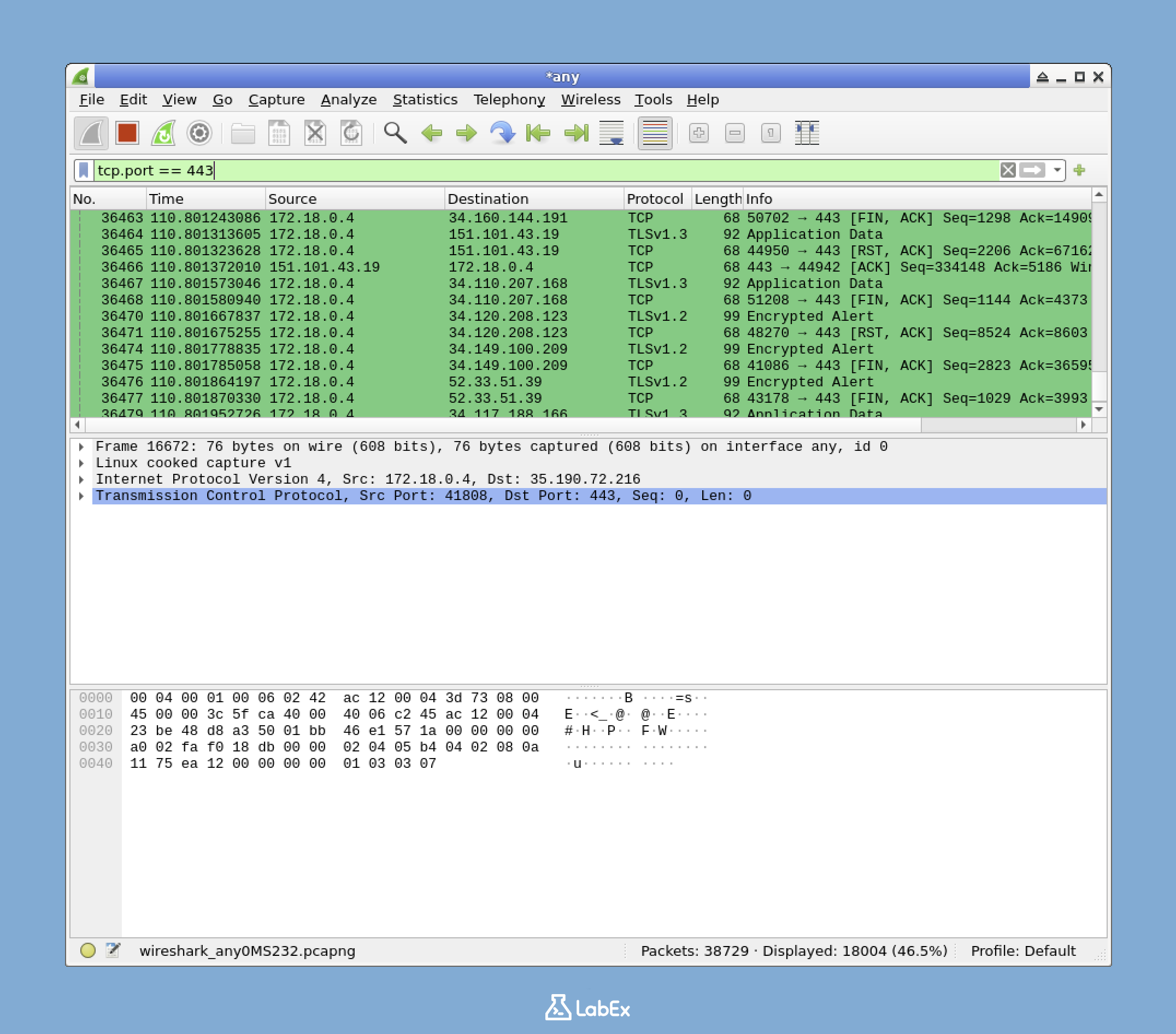
Introduction
In this challenge, you will take on the role of a junior cybersecurity analyst at SecureNet tasked with monitoring encrypted web traffic on your organization's network. Your objective is to create a custom colorizing rule in Wireshark that highlights all HTTPS traffic (TCP port 443) with a green background and black text, making secure web connections easily identifiable during packet analysis.
This hands-on exercise will guide you through launching Wireshark, accessing the Coloring Rules dialog, creating and configuring a new rule named 'Secure Web Traffic', and finally exporting your customized colorizing rules to a file. By completing this challenge, you'll enhance your ability to quickly identify secure communications in network traffic—a crucial skill for effective cybersecurity monitoring.