Introduction
In this project, you'll learn how to create a reverse shell using Python, which allows you to control multiple compromised machines, also referred to as "bots". Unlike traditional shells, a reverse shell initiates a connection from the bot to the controller, enabling management of remote hosts even behind firewalls or NAT. This method is widely used in cybersecurity practices for penetration testing and managing controlled environments in a secure manner.
Before diving into the implementation, it's important to understand the foundational concepts behind our reverse shell application, including the client-server (C/S) architecture and the Transmission Control Protocol (TCP).
The C/S architecture involves a client that requests services and a server that provides services. In our case, the bots act as clients initiating connections to our server, allowing us to execute commands on them remotely.
We'll use TCP for reliable, connection-oriented communication between the server and clients. TCP ensures that data is delivered accurately and in order, which is essential for executing commands and receiving responses without errors.
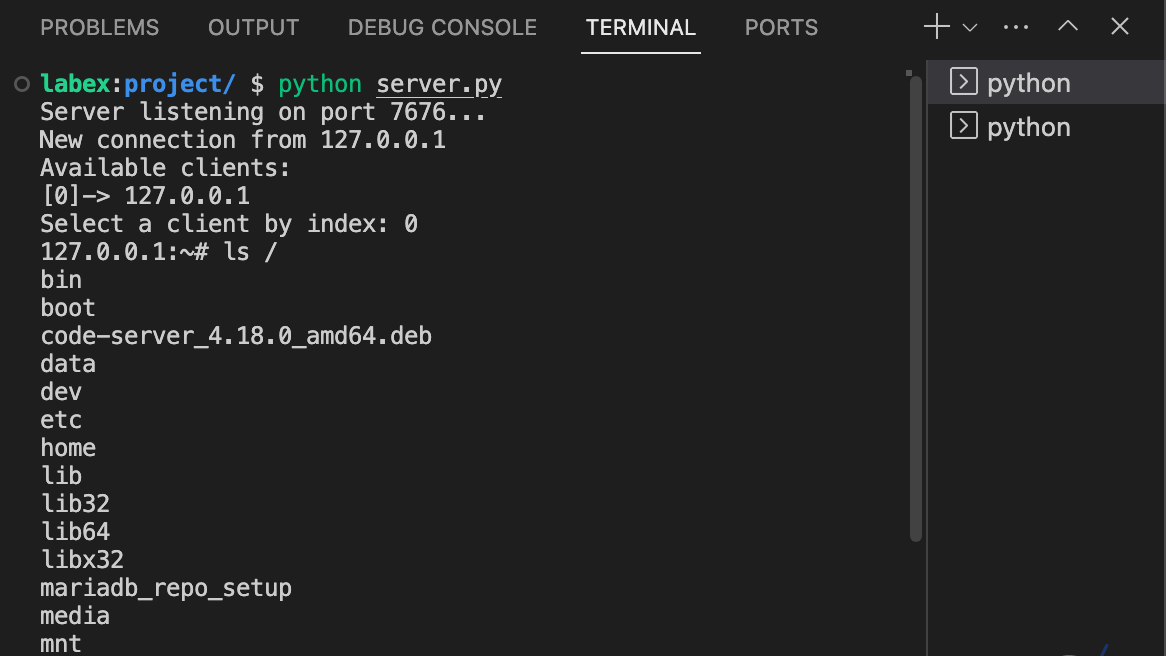
👀 Preview
🎯 Tasks
In this project, you will learn:
- How to understand the client-server (C/S) architecture and the Transmission Control Protocol (TCP) as the foundation for network communications.
- How to set up a server that listens for incoming connections from multiple clients (bots).
- How to create client scripts that connect to the server and execute received commands.
- How to implement command execution and result retrieval functionality on the server to interact with the connected clients.
- How to manage multiple client connections simultaneously and switch between them to issue commands.
🏆 Achievements
After completing this project, you will be able to:
- Demonstrate mastery of the basics of the client-server model and TCP for reliable network communication.
- Implement a multi-client reverse shell server in Python.
- Create client scripts that can connect to a remote server and execute commands sent from the server.
- Handle multiple connections and manage communication with multiple clients in a controlled environment.
- Apply practical experience in network programming and an understanding of its applications in cybersecurity and remote system management.