Introduction
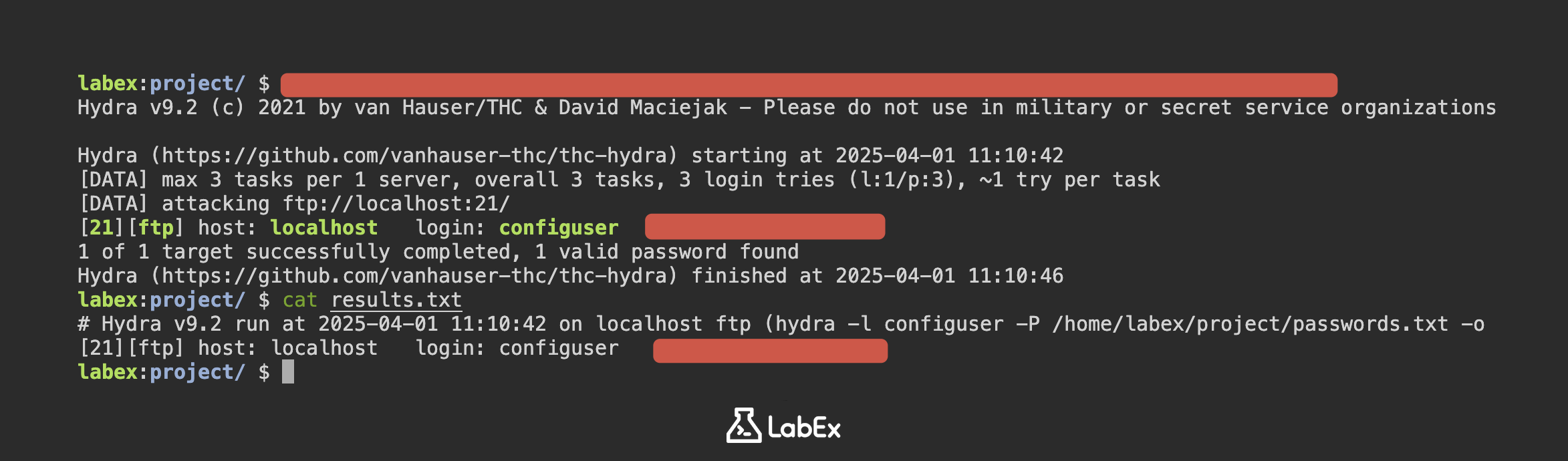
In this challenge, you'll be tasked with cracking a rogue employee's FTP server using Hydra and a custom wordlist. The scenario involves a weakly secured FTP server running on the company network, and your objective is to identify the password and secure the server.
The challenge involves setting up a vulnerable FTP server using vsftpd, creating a user named configuser with a known password, and then crafting a custom password list file named passwords.txt containing potential passwords like "config1", "config123", and "password". Finally, you'll use Hydra to brute-force the FTP password for the configuser account on localhost using your custom password list, aiming to identify the correct password and demonstrate the vulnerability.