Introduction
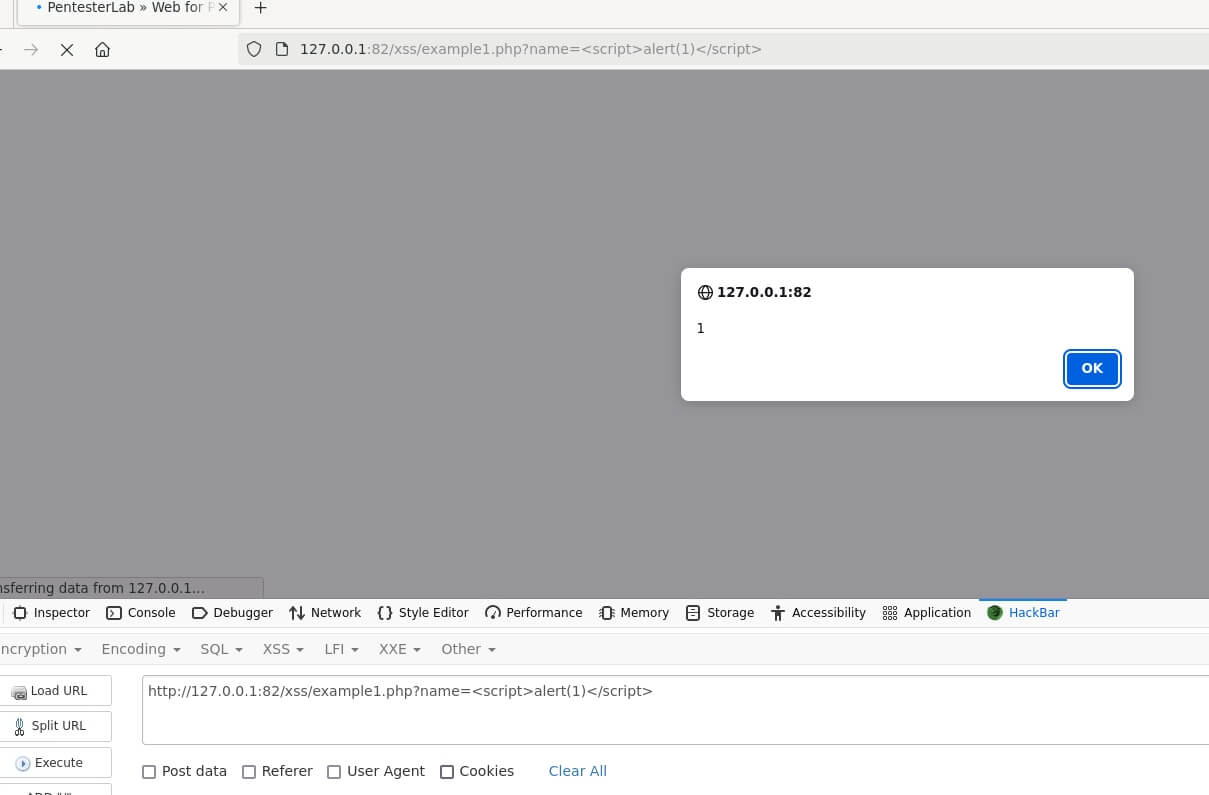
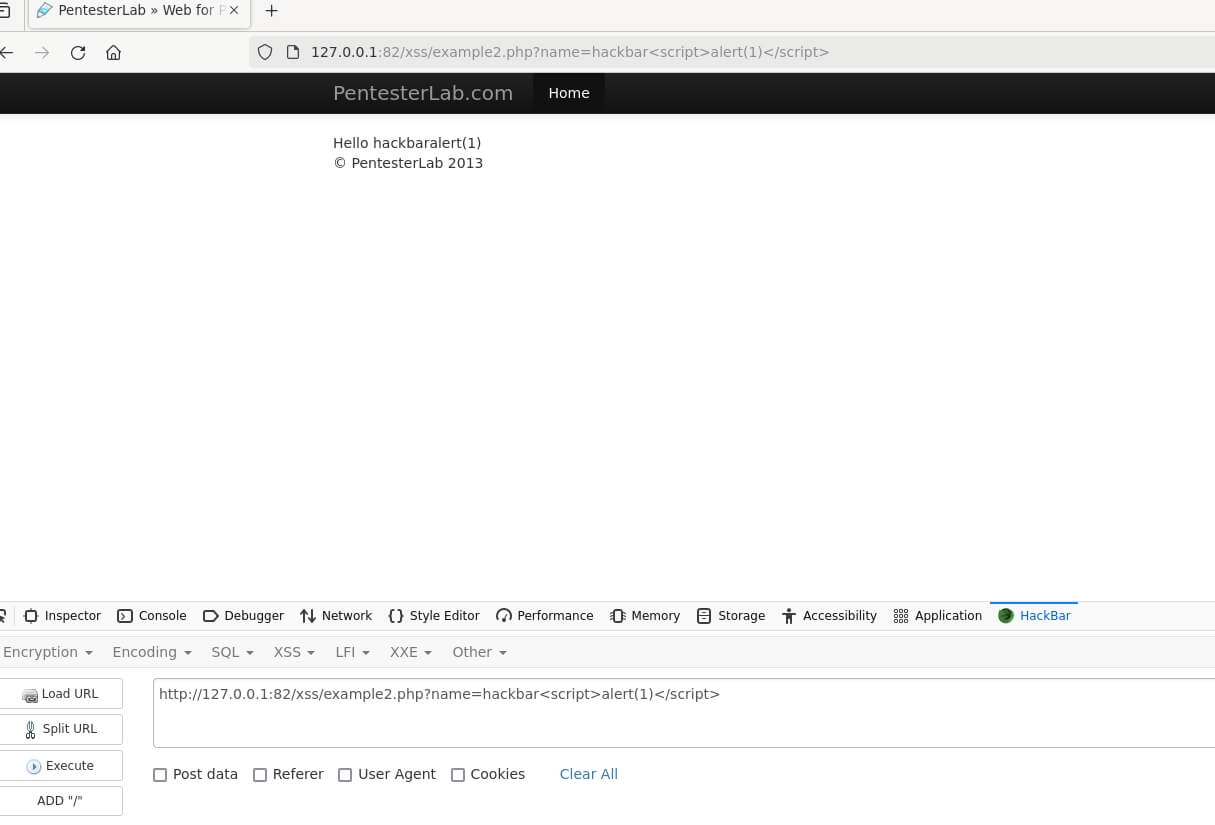
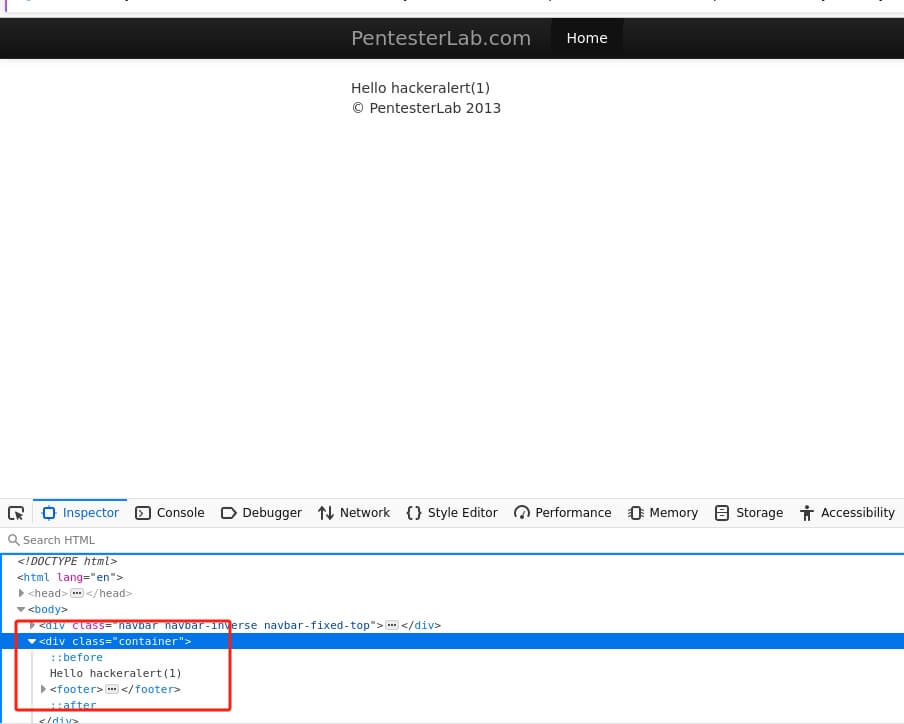
Welcome to our interactive lab! Here, we'll dive into the world of web security by focusing on Cross-Site Scripting (XSS) - a common but crucial vulnerability in web applications. If a website isn't properly protected against XSS, it can become a playground for attackers.
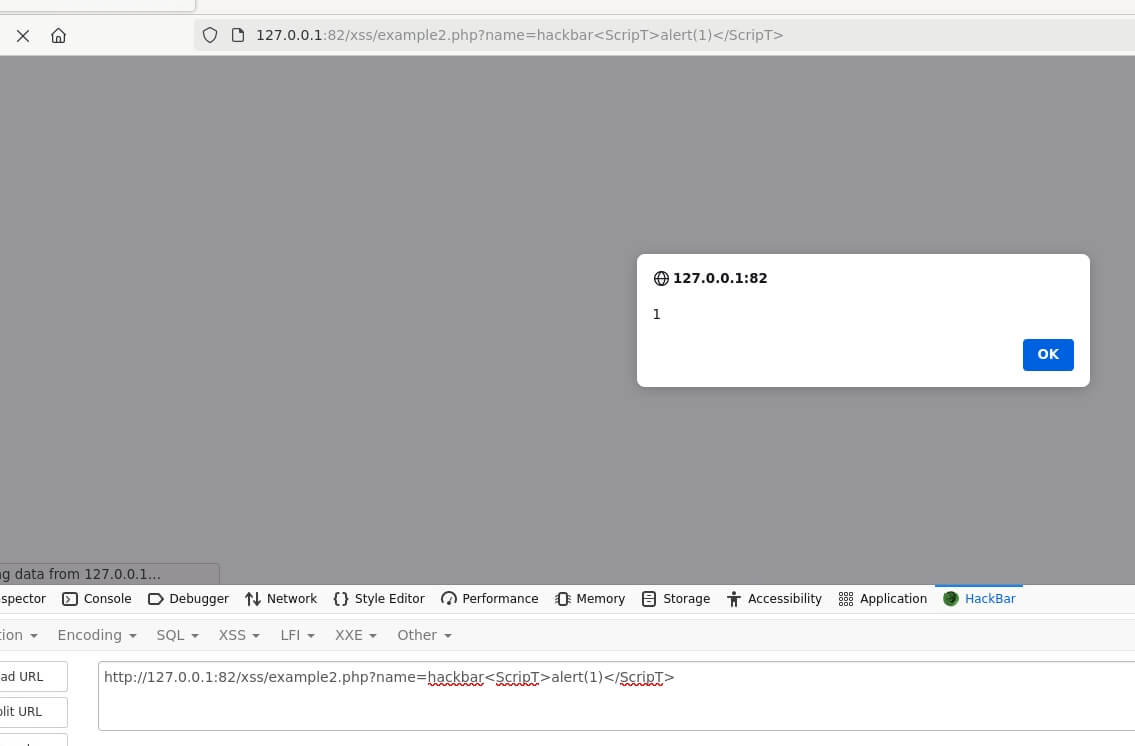
But don't worry! We're going to help you understand and tackle this issue. We'll start by breaking down what XSS is, why it's important, and how it can be exploited. We'll then guide you through using a tool called 'hackbar', which will assist us in identifying potential XSS vulnerabilities.
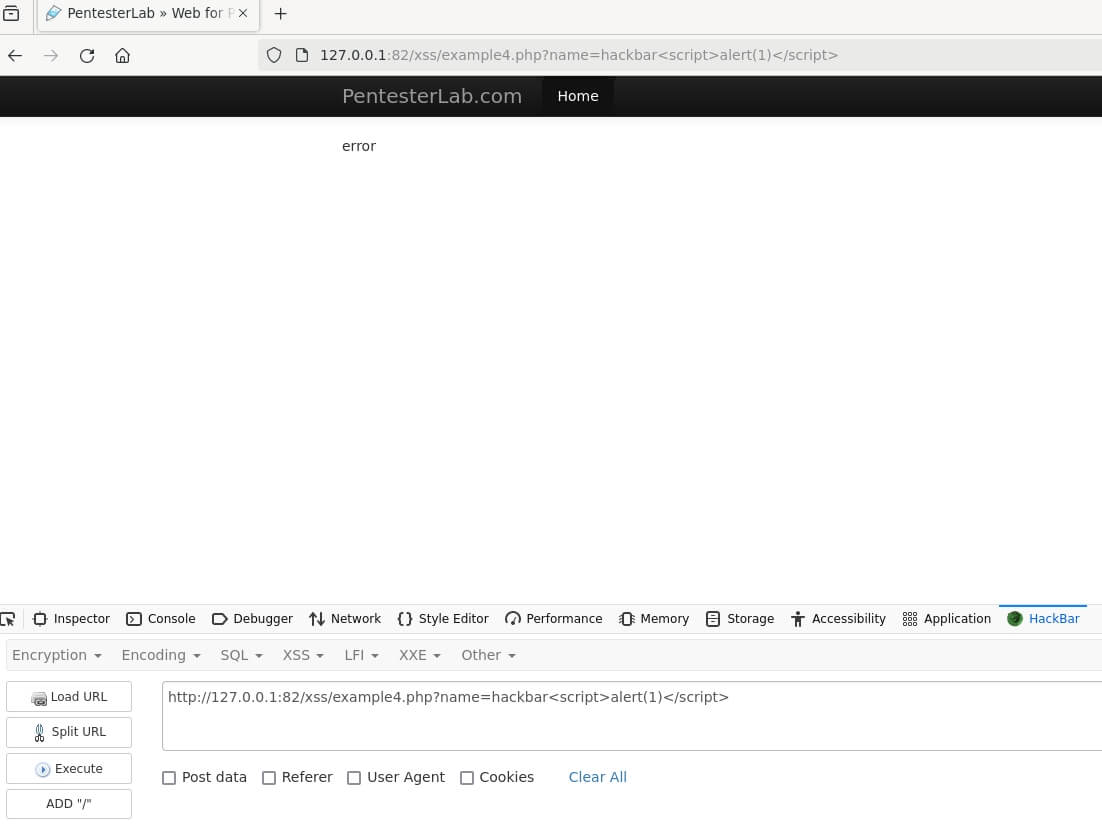
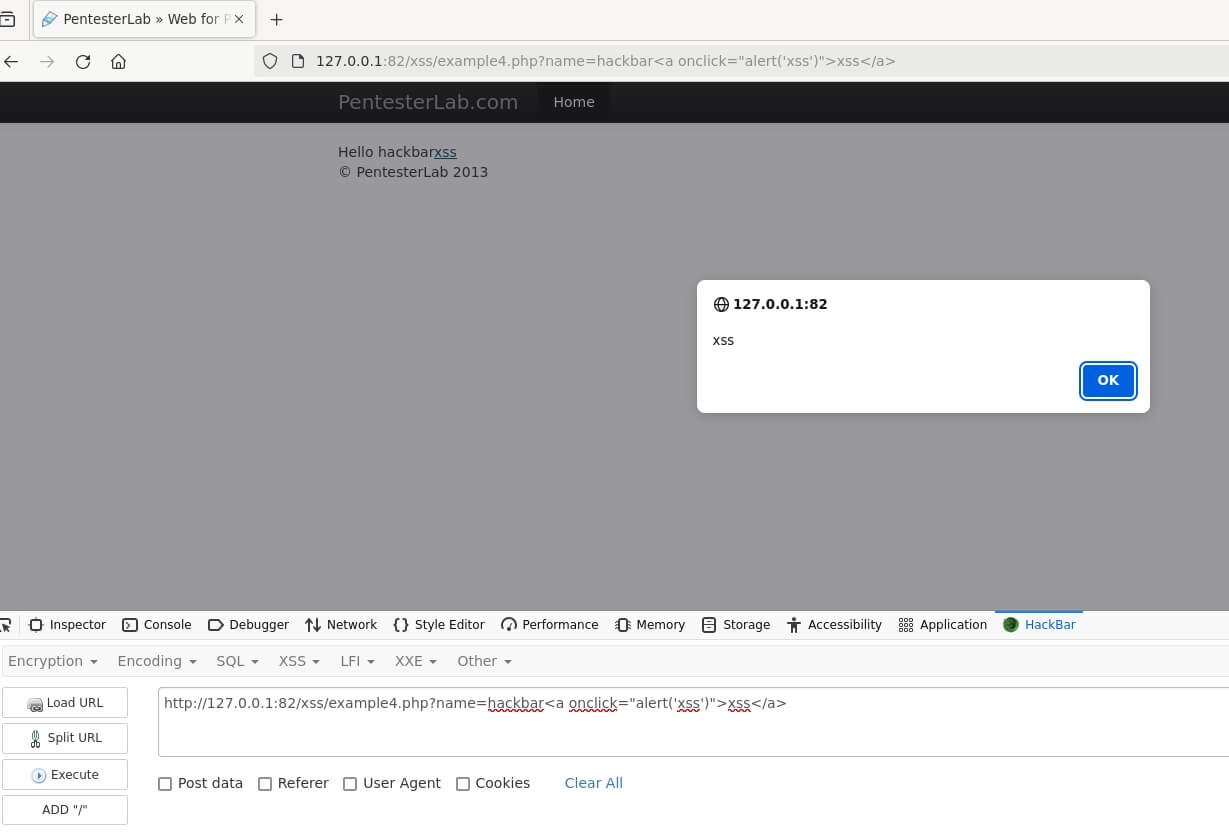
In addition, we'll also explore various 'bypassing techniques'. These are clever methods that attackers can use to circumvent security measures, and by understanding them, we can better protect our websites.
Remember, the best way to learn is by doing - so we'll be conducting hands-on experiments throughout. By the end of this lab, you'll have a solid understanding of XSS vulnerabilities and how to prevent them. Let's get started!