Introduction
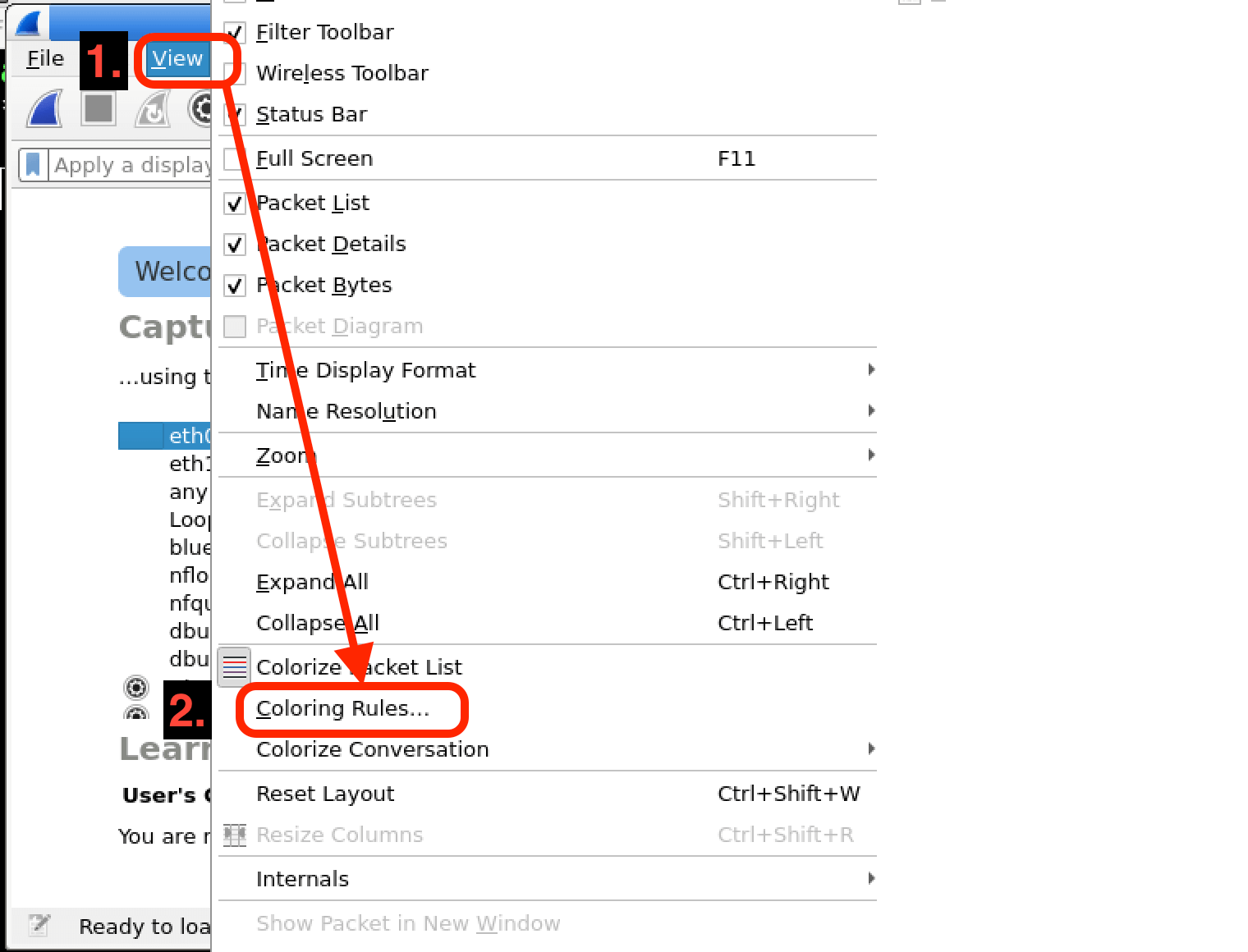
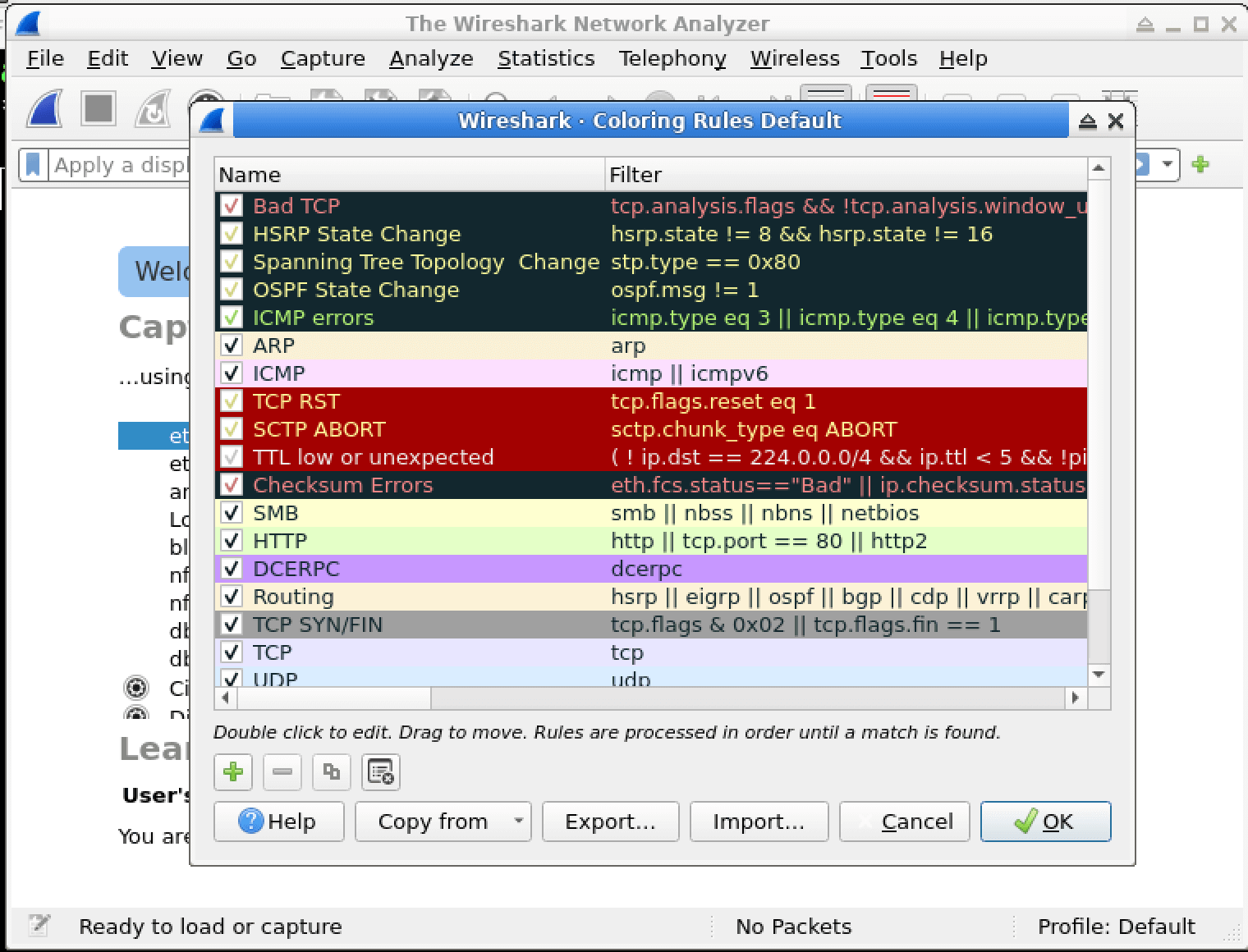
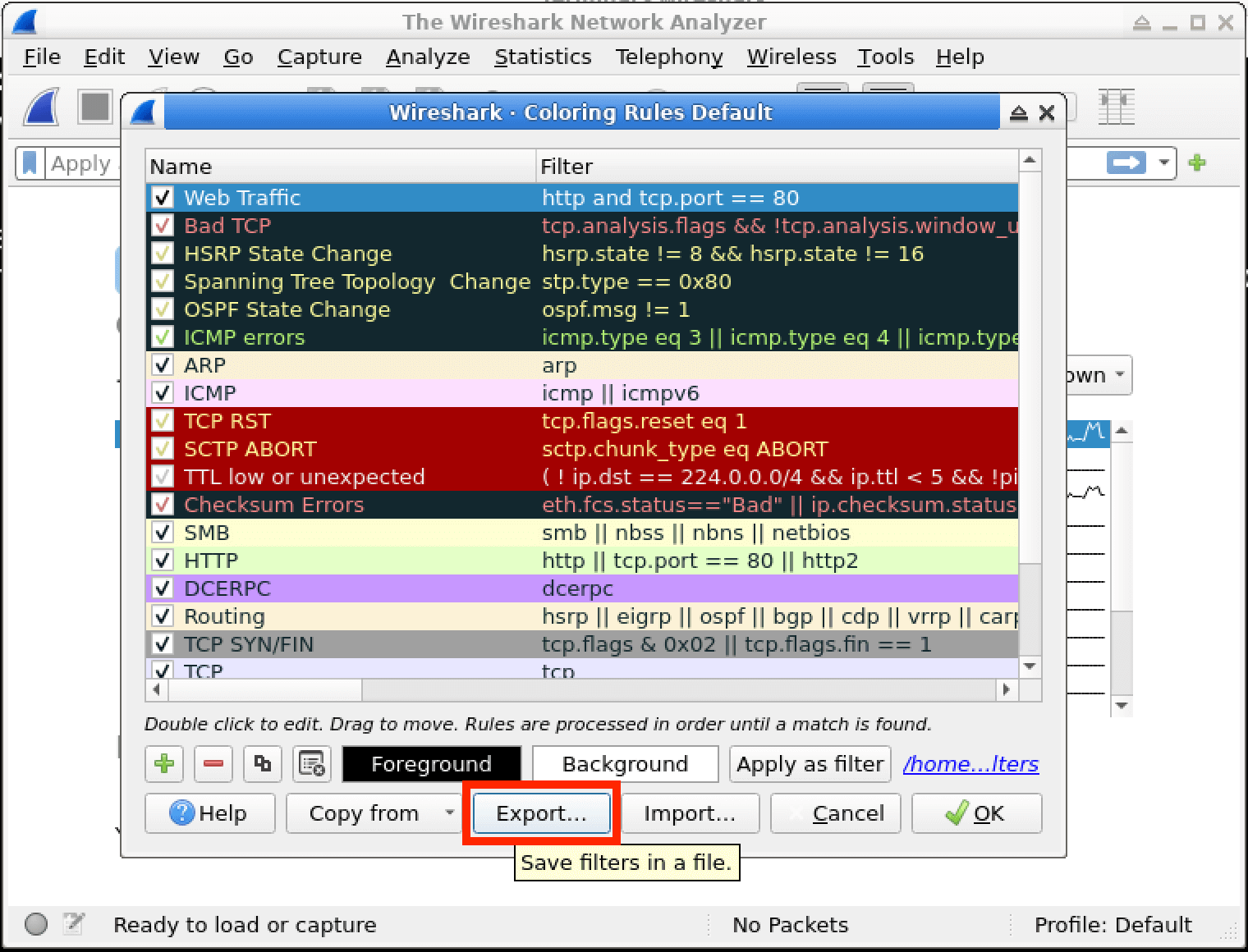
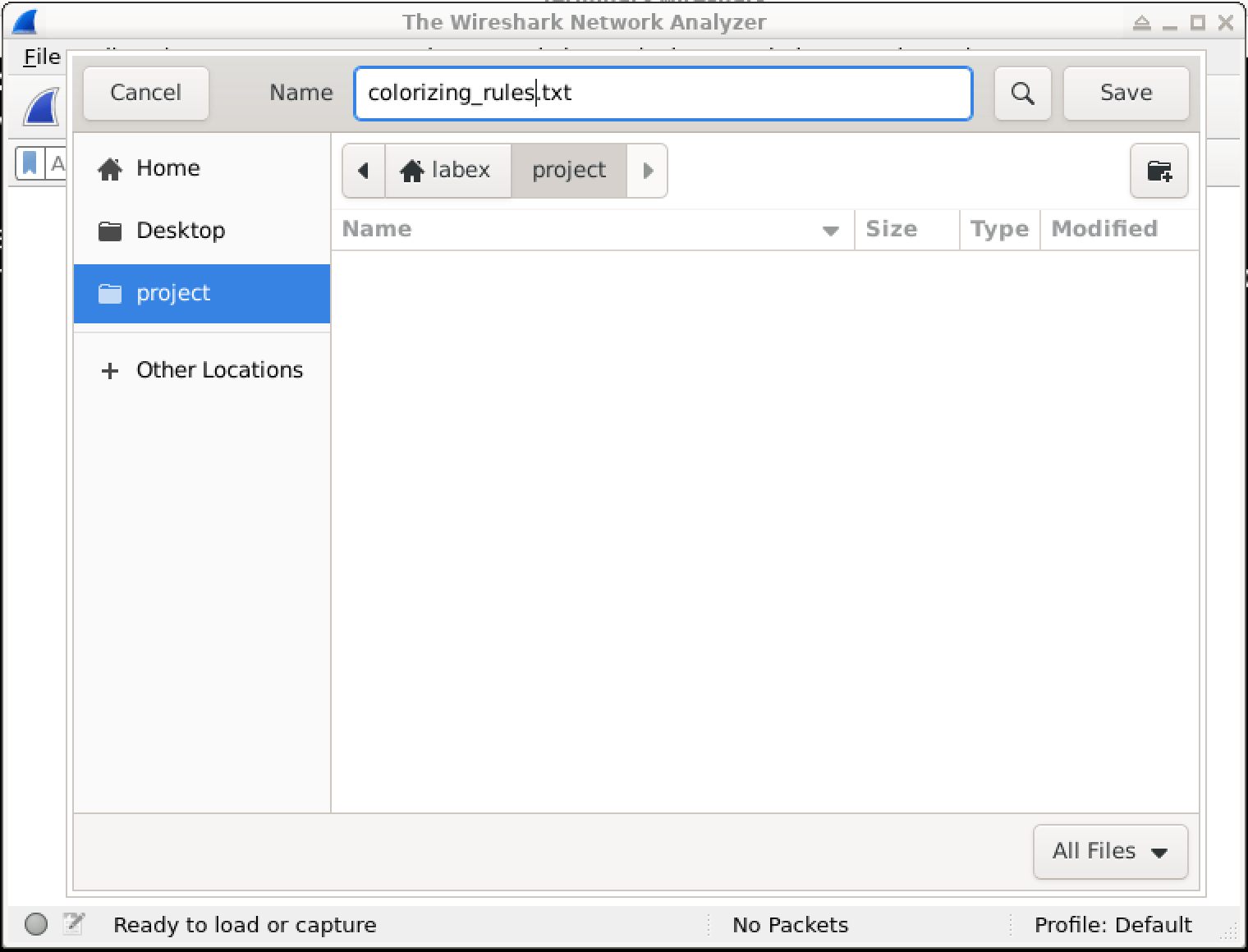
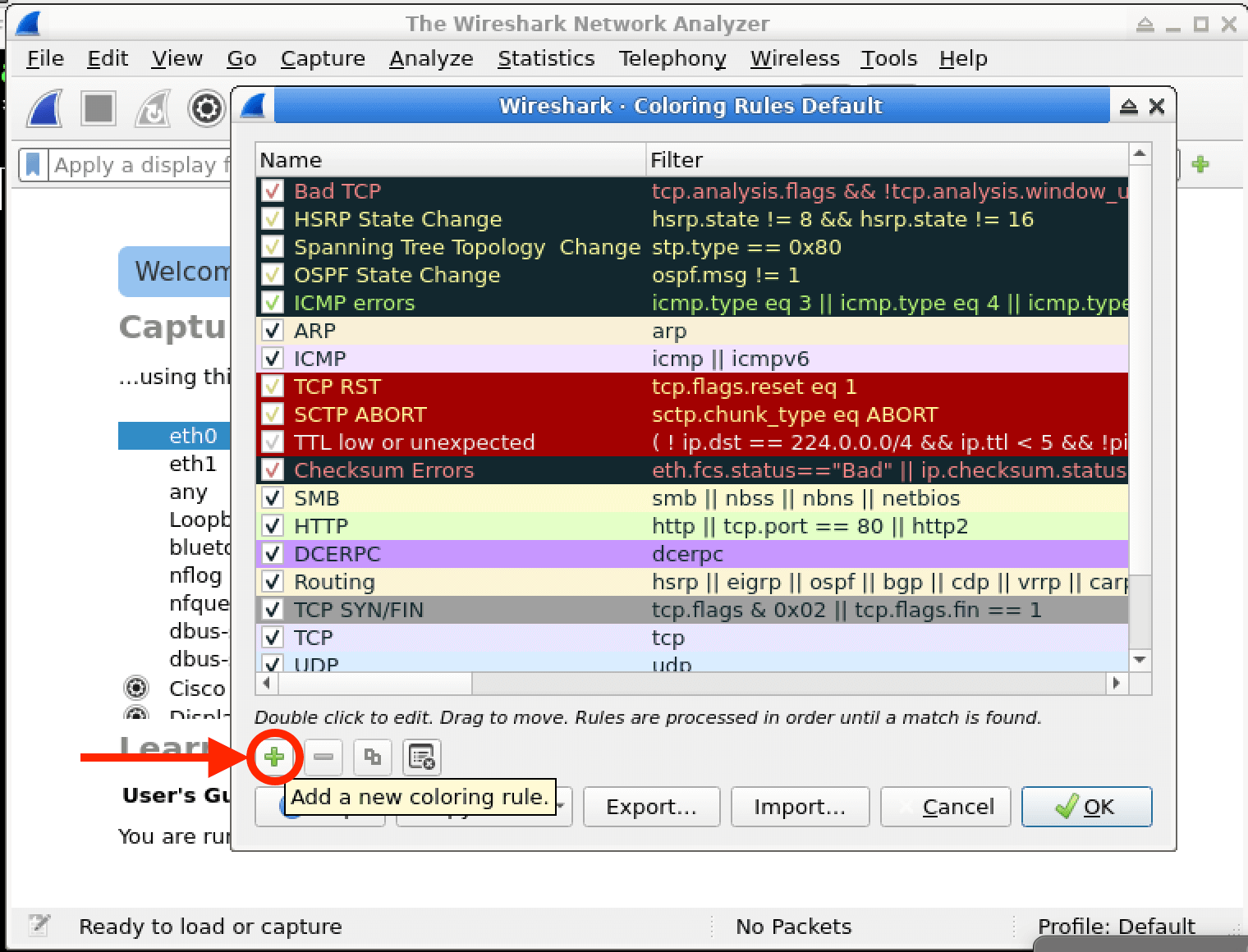
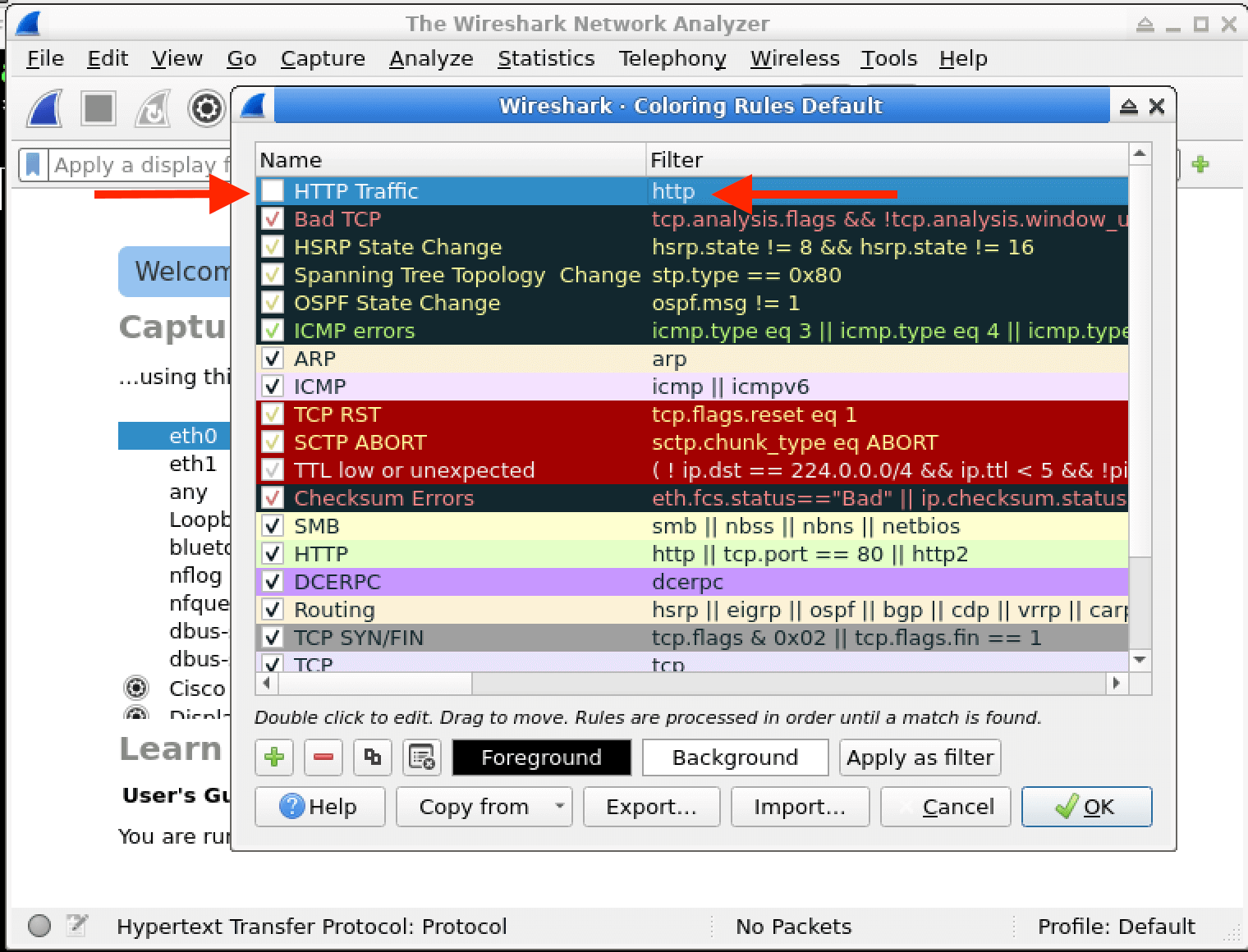
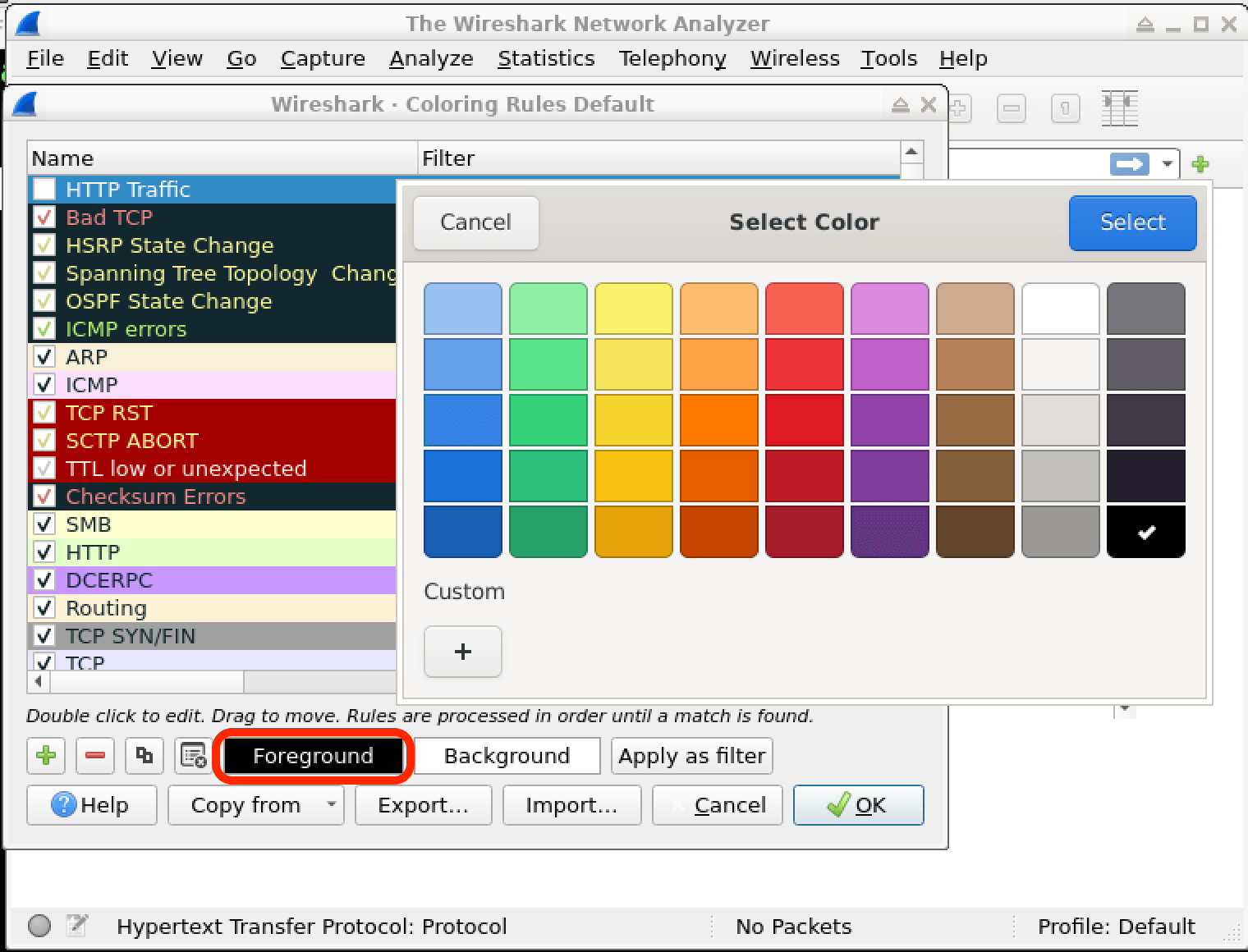
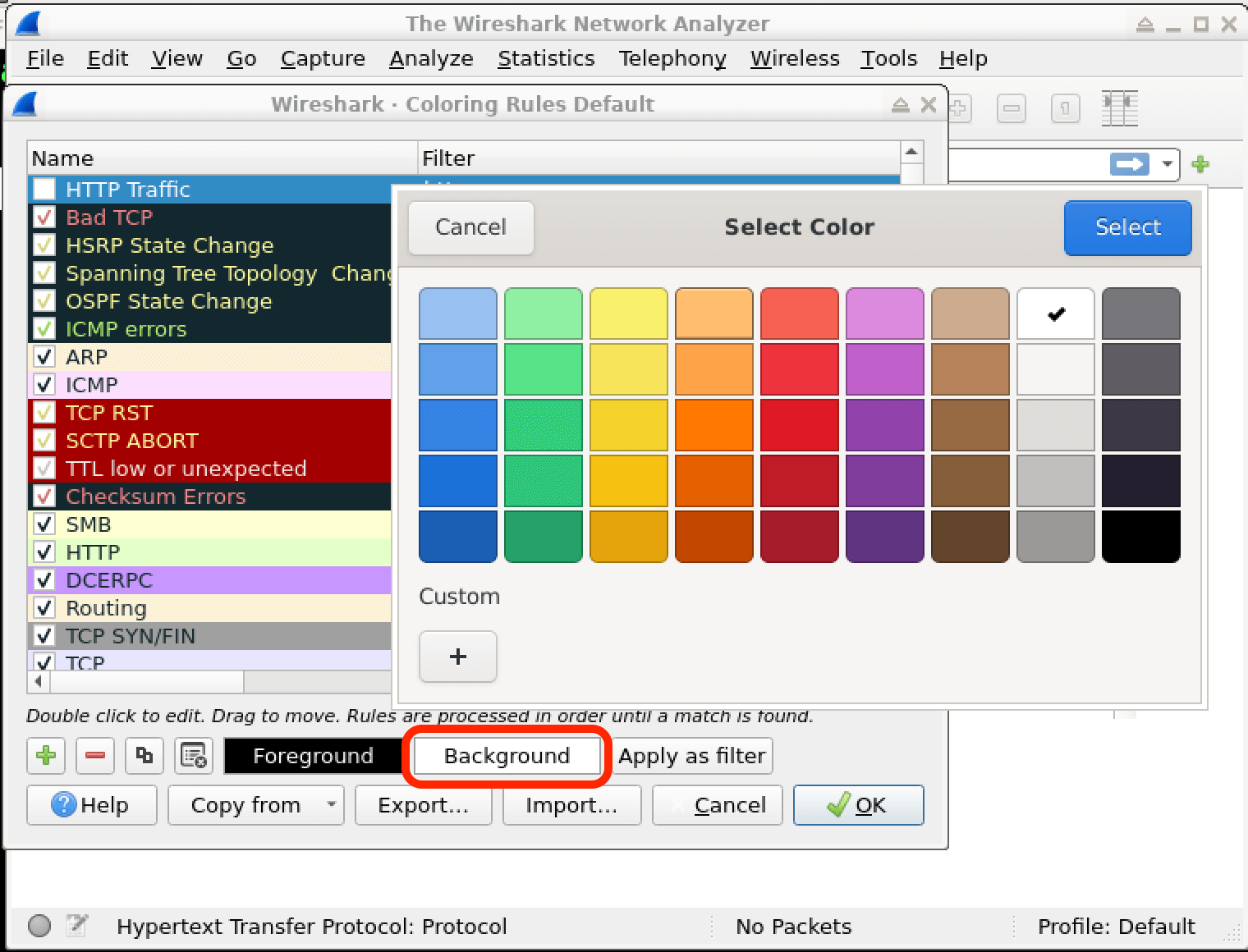
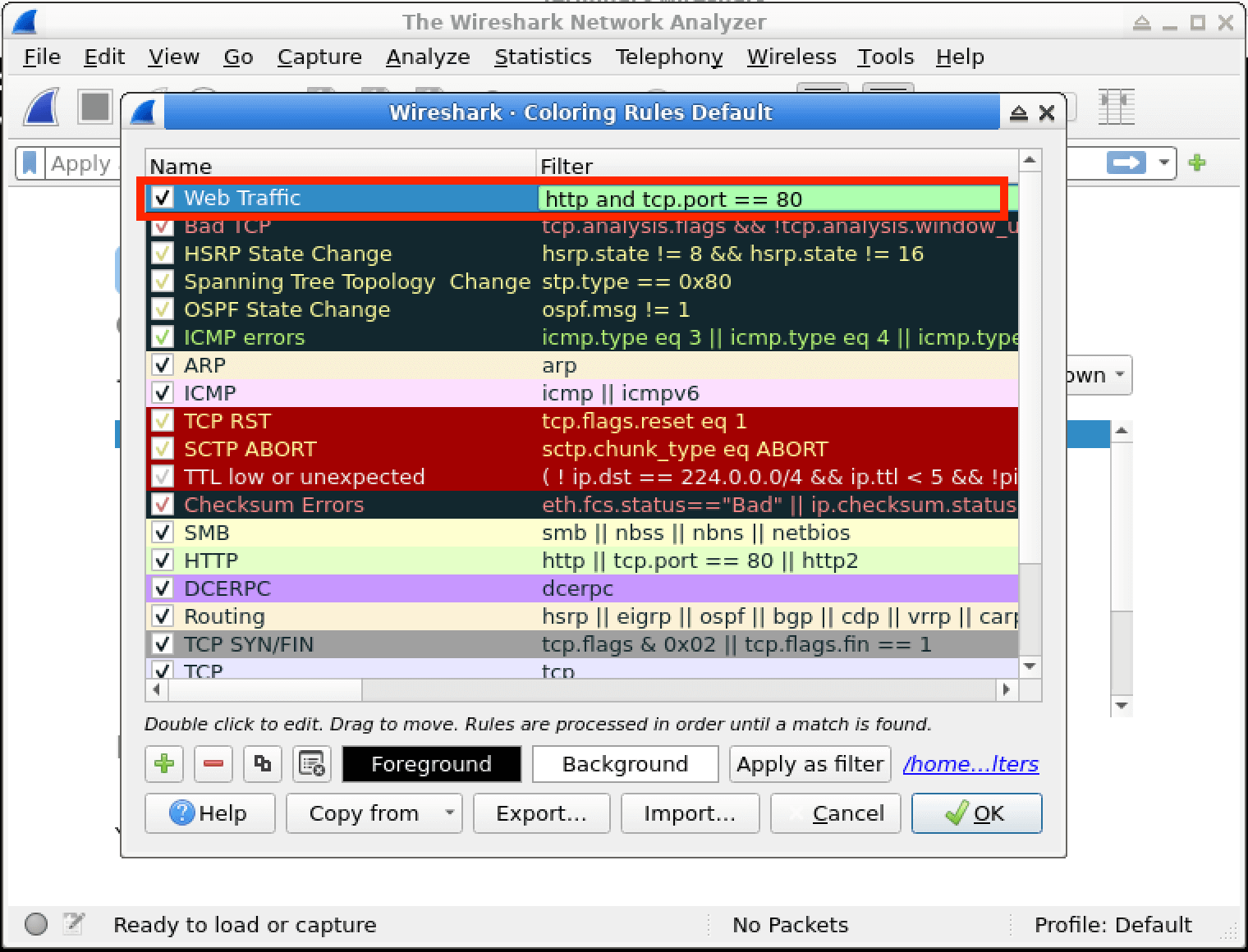
In this lab, you will learn how to create and apply colorizing rules in Wireshark, a powerful network protocol analyzer. Colorizing rules allow you to visually distinguish different types of network traffic based on specific criteria, making it easier to identify and analyze network activities of interest. By the end of this lab, you will have a better understanding of how to leverage Wireshark's colorizing capabilities to enhance your network analysis and cybersecurity investigations.