Introduction
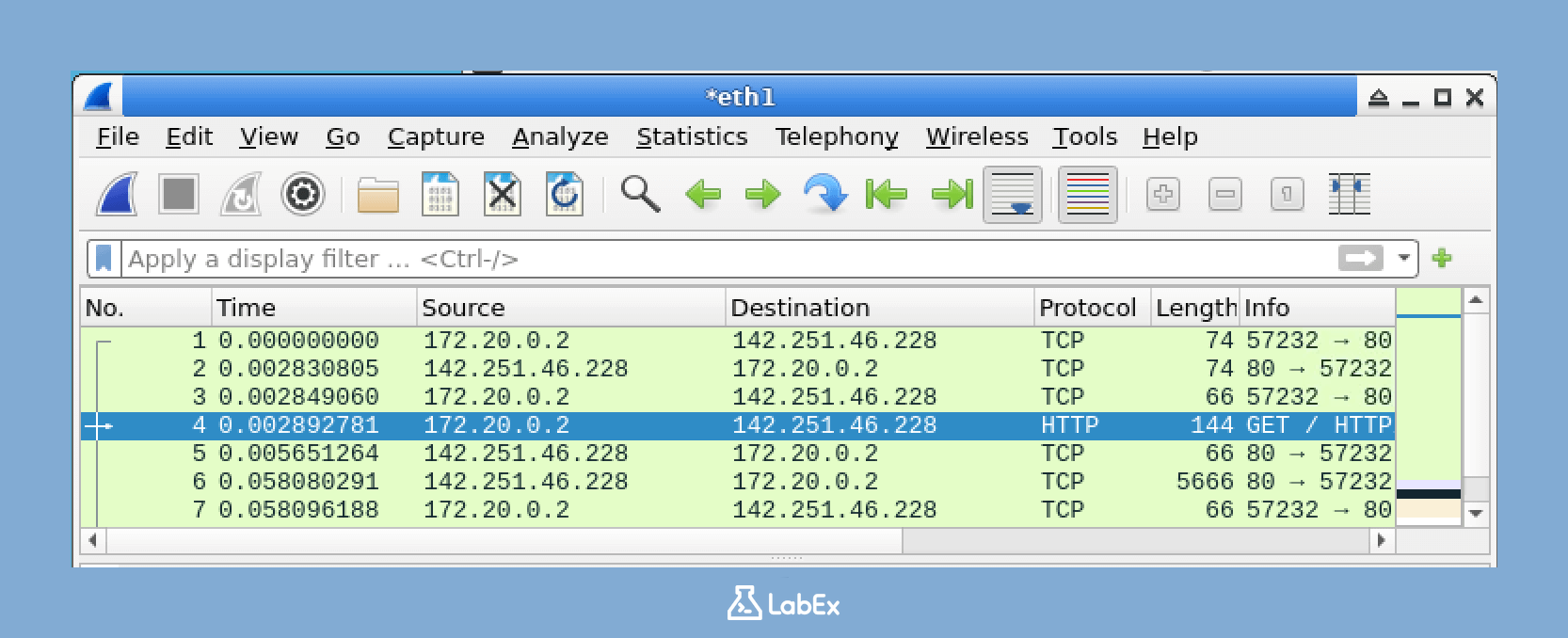
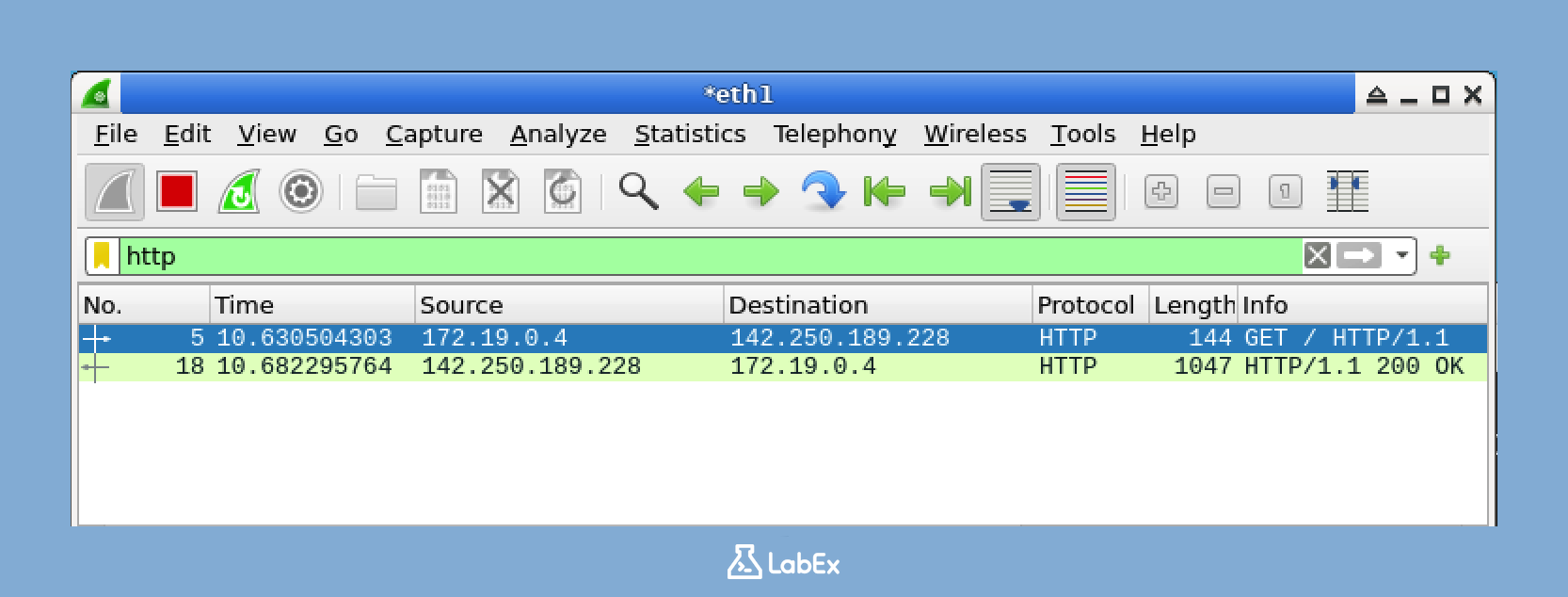
In this lab, you will learn how to use Wireshark display filters to analyze network traffic and identify potential security threats. Wireshark is a powerful network protocol analyzer that can capture and dissect network packets, making it an essential tool for cybersecurity professionals. By mastering Wireshark display filters, you will be able to quickly isolate and inspect specific types of traffic, streamlining your analysis efforts and enhancing your ability to detect and respond to security incidents.