Introduction
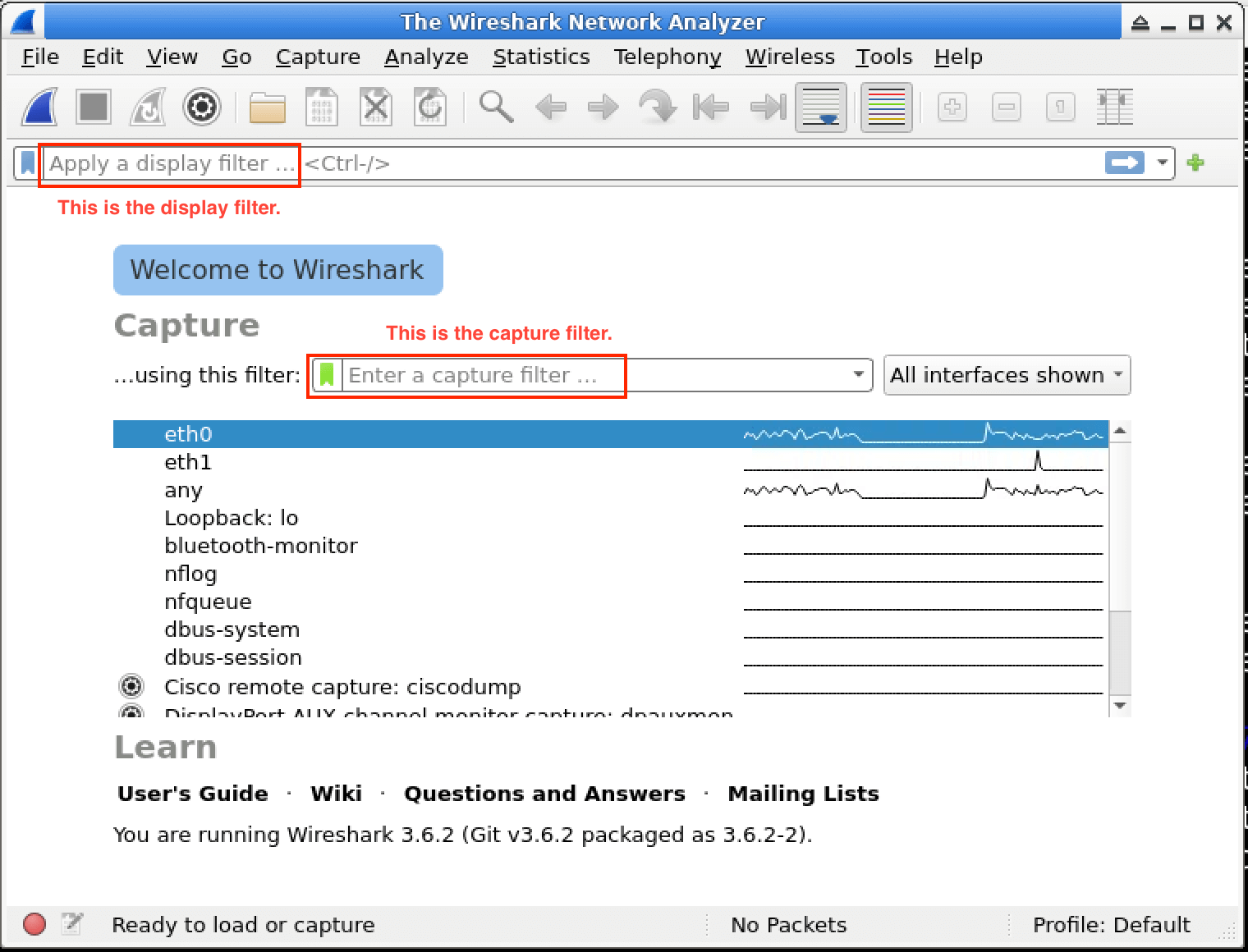
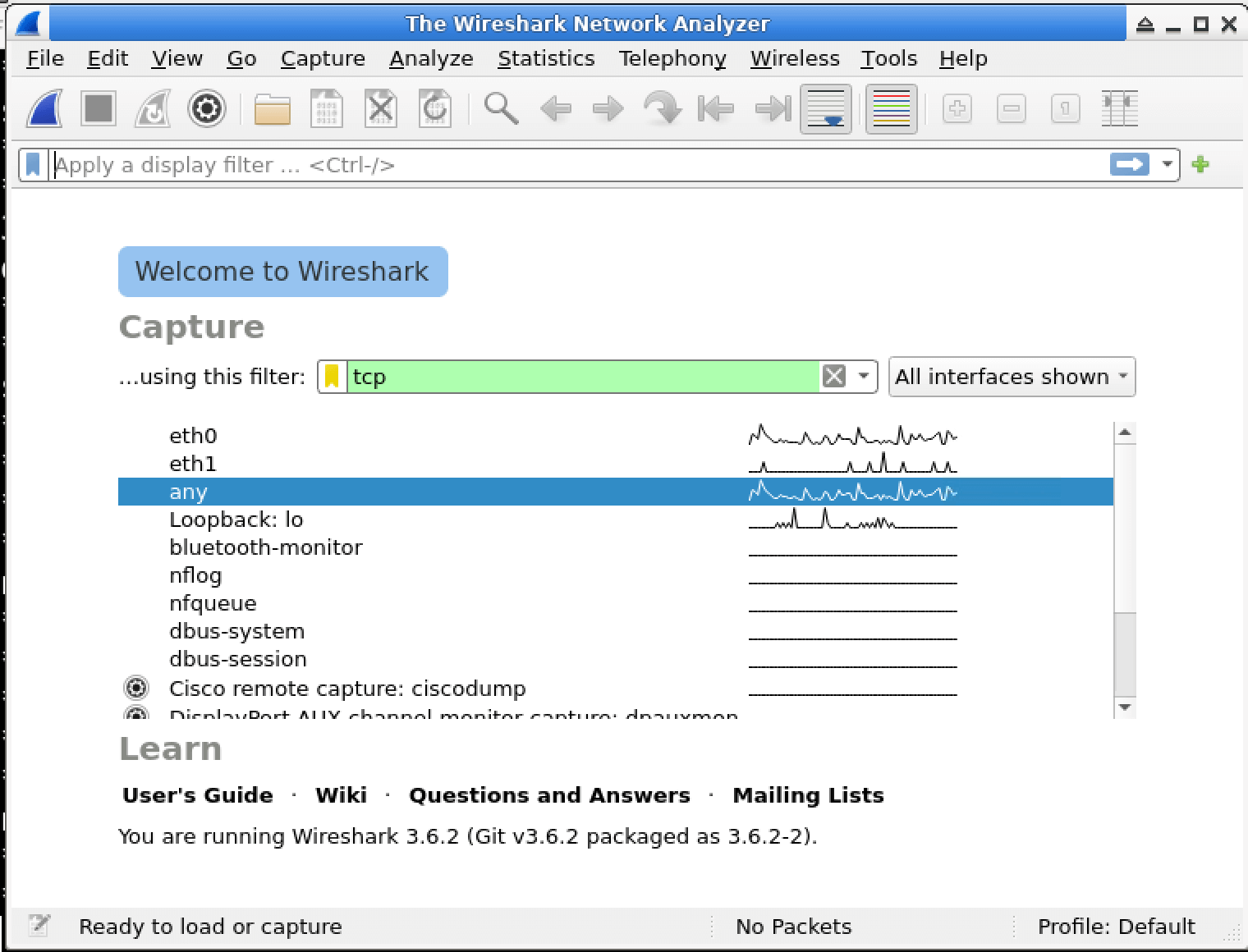
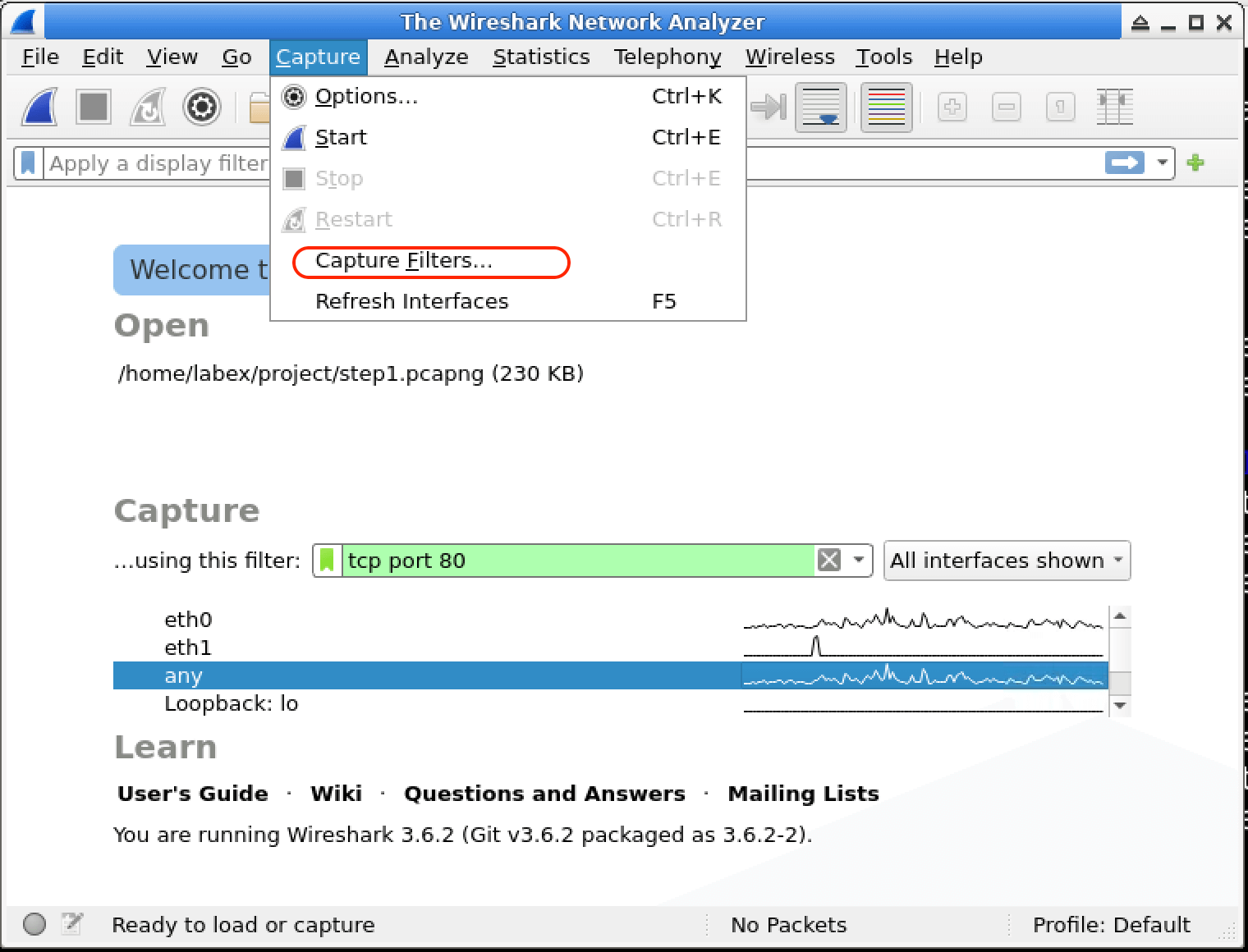
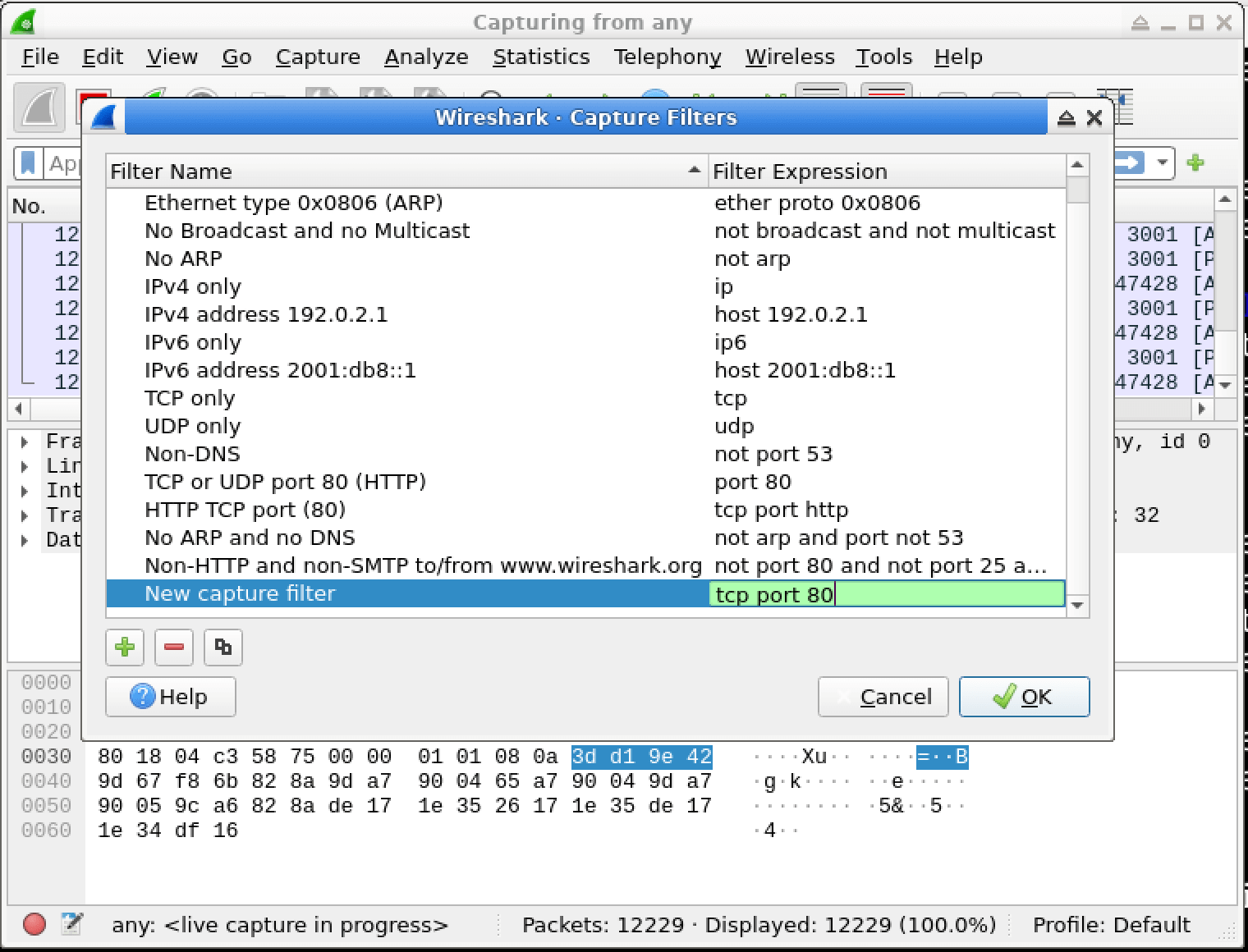
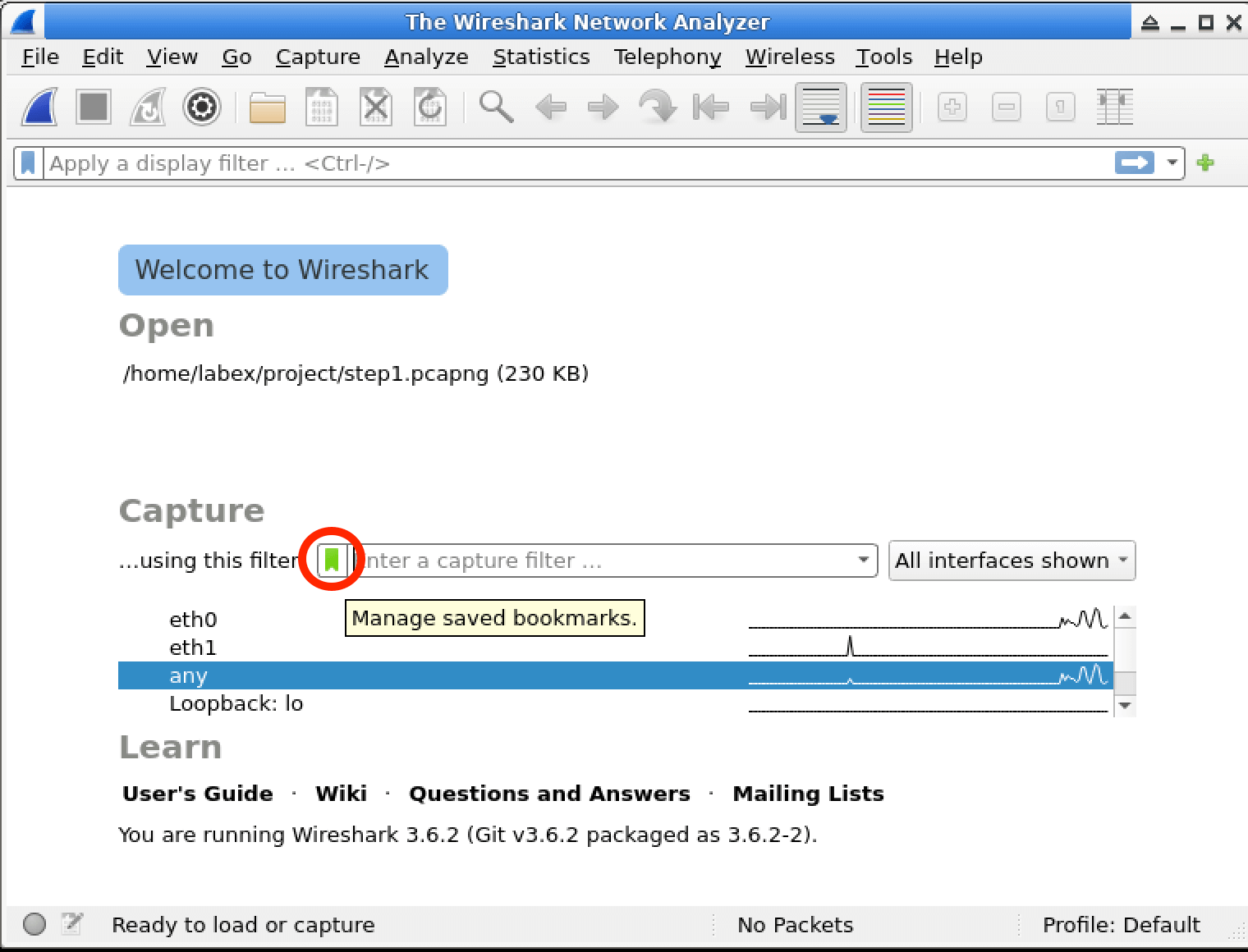
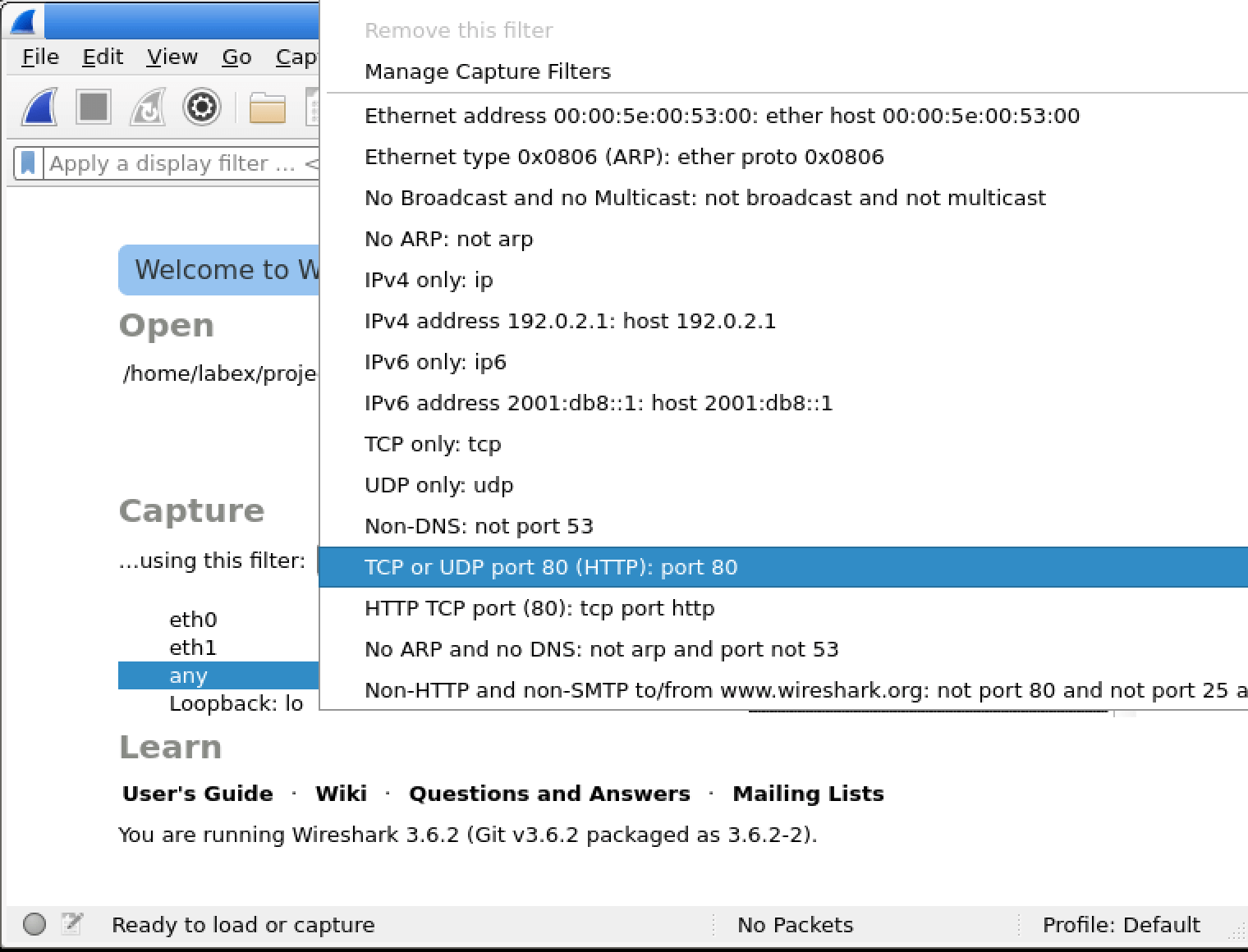
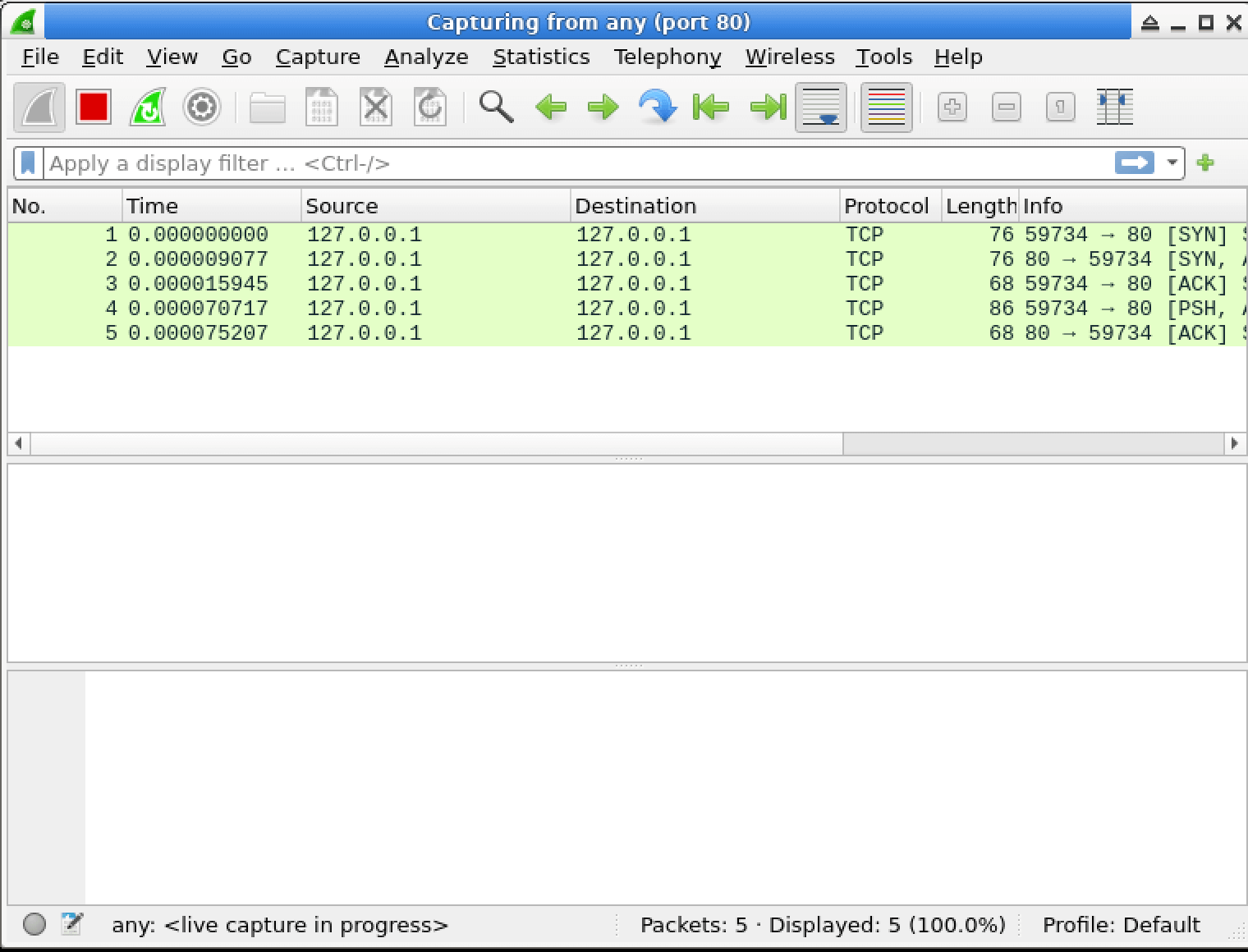
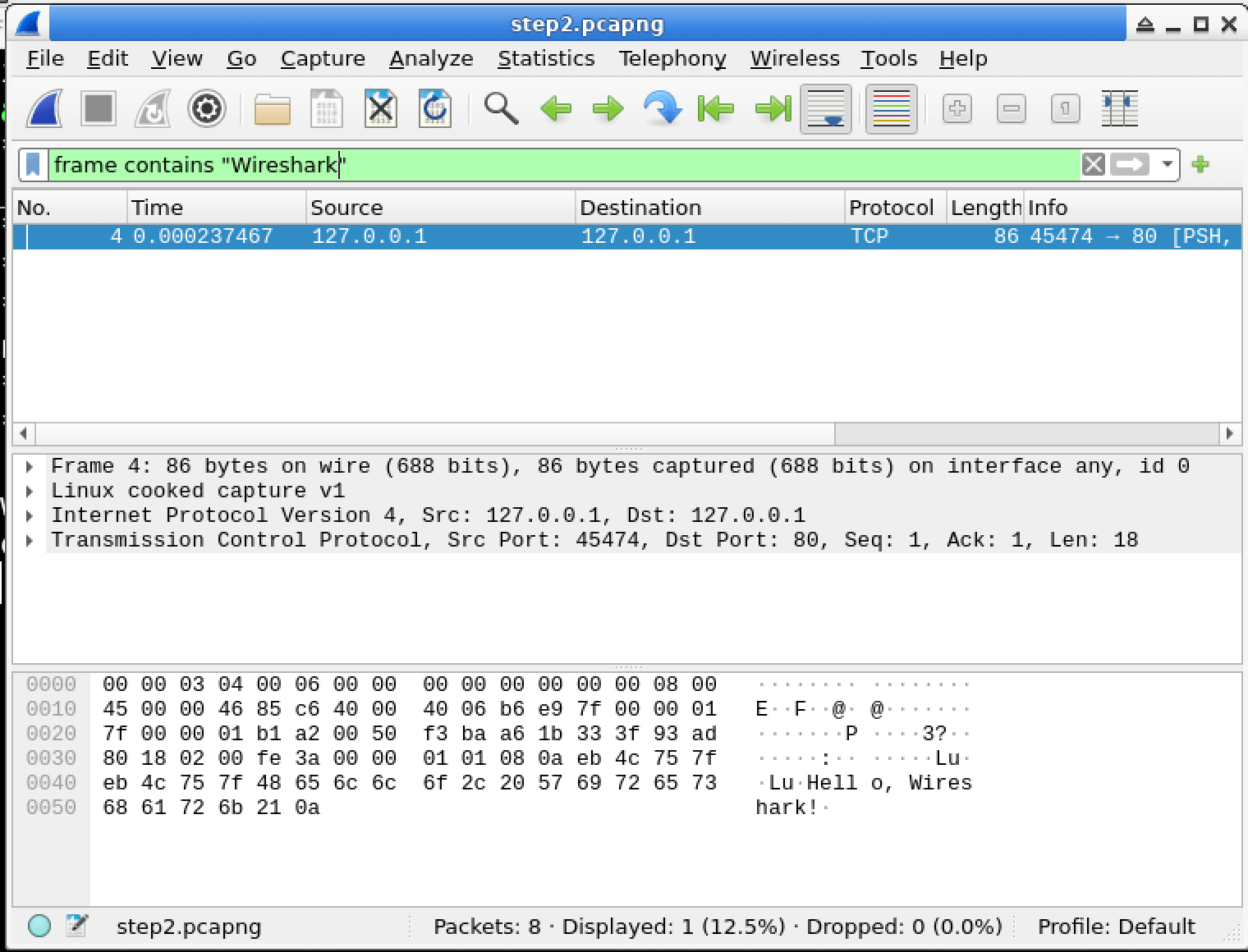
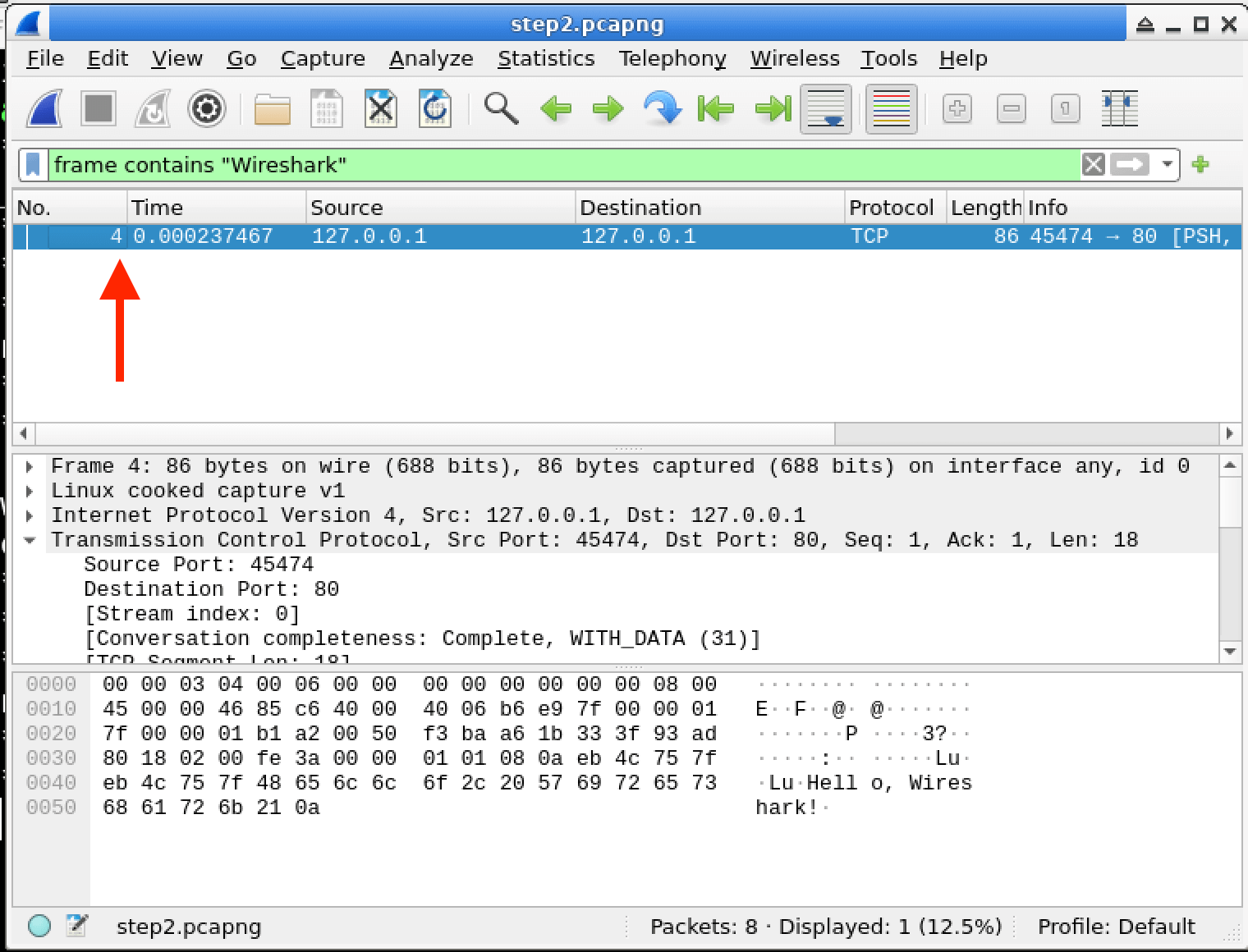
In this lab, you will learn how to use Wireshark capture filters to selectively capture network traffic based on specific criteria. Capture filters are powerful tools that allow you to focus on relevant data and discard irrelevant traffic, making your analysis more efficient and effective. You will explore various capture filter expressions and apply them to real-world scenarios, enhancing your skills in network troubleshooting and security analysis.